Hello @Giri Rajh ,
Thanks for the question and using MS Q&A platform.
As we understand the ask here is "How do I allow a service principal to create new files in a directory, but not allow deletion of files in same directory?"
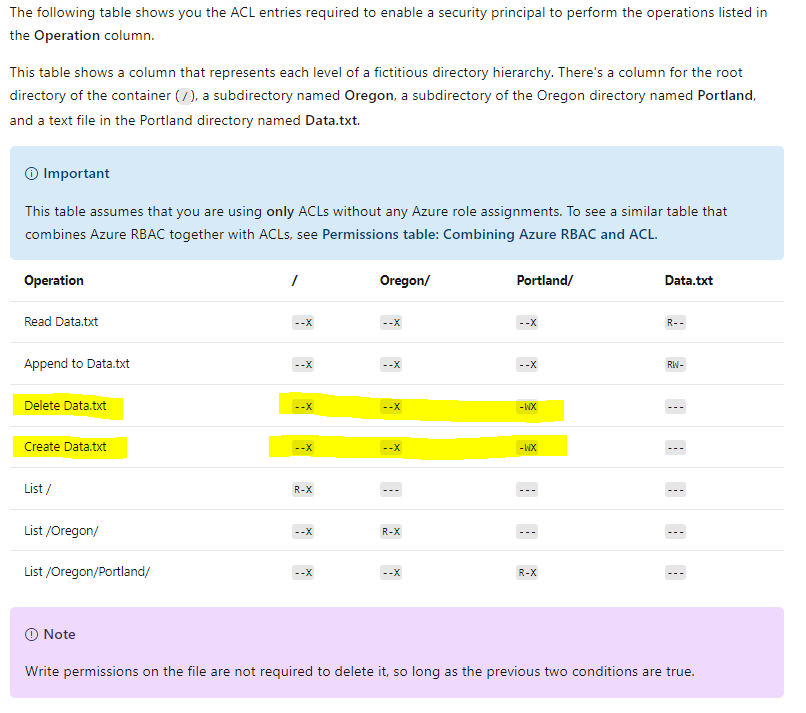
You have found the create and delete file operations have exactly the same permissions. The short answer is, I don't think you can allow one without the other in this cloud situation. (I vaguely recall accomplishing your ask back in college, but in that system, the write and execute permissions on file mattered. The purple note you showed says otherwise.)
Assumption: you own the directory, not the customer's pervice principal.
However I do have a couple of options. First, the invisible sticky bit:
The sticky bit is a more advanced feature of a POSIX container. In the context of Data Lake Storage Gen2, it is unlikely that the sticky bit will be needed. In summary, if the sticky bit is enabled on a directory, a child item can only be deleted or renamed by the child item's owning user, the directory's owner, or the Superuser ($superuser).
The sticky bit isn't shown in the Azure portal.
The sticky bit would help if you had multiple users/service principals writing to the same directory. This would prevent them from deleting other user's files, but still allow them to delete their own file.
You could then have an automation change the file owner property to a service principal under your control. This would take away their ability to delete the file while sticky bit is enabled.
Another option would be to use a staging area. Any files dropped into the staging would be moved to the desired directory by an application/service principal under your control. By allowing users to deposit in the staging area, but forbidding them from the destination directory, you keep the files safe from their meddling.
Please do let me if you have any queries.
Thanks
Martin
------------------------------------------
- Please don't forget to click on
 or upvote
or upvote  button whenever the information provided helps you. Original posters help the community find answers faster by identifying the correct answer. Here is how
button whenever the information provided helps you. Original posters help the community find answers faster by identifying the correct answer. Here is how