
Hi @Rajeshkumar I ,
There are some settings about IIS to prevent version disclosure.
- Disable directory listing to prevent attacker get the file struction of site and server appcmd set config /section:directoryBrowse /enabled:false
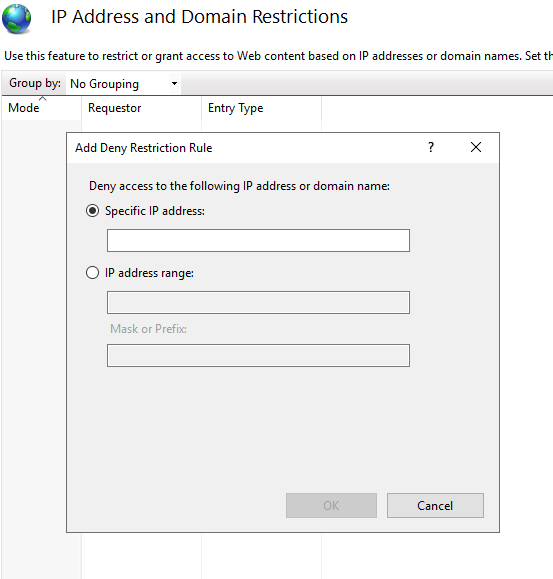
- Restrict user or IP access for some specific directories or urls.
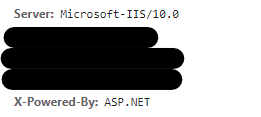
- Some response headers will expose server and web application information. Such as
X-Power-ByandServer. Remove them or rewrite its value.
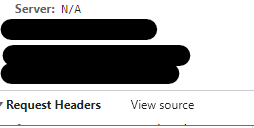
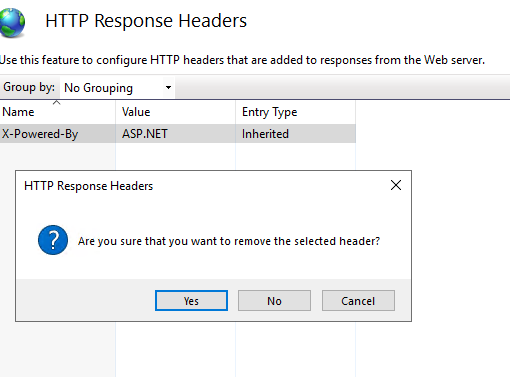 <rewrite>
<rewrite>
<outboundRules>
<rule name="remove server headers">
<match serverVariable="RESPONSE_Server" pattern=".*" />
<action type="Rewrite" value="N/A" />
</rule>
</outboundRules>
</rewrite>
If the answer is the right solution, please click "Accept Answer" and kindly upvote it. If you have extra questions about this answer, please click "Comment".
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.
Best regards,
Bruce Zhang