How to connect Virtual Machine in Azure with LANCOM vRouter via local Lancom VPN Gateway?
Hey everyone,
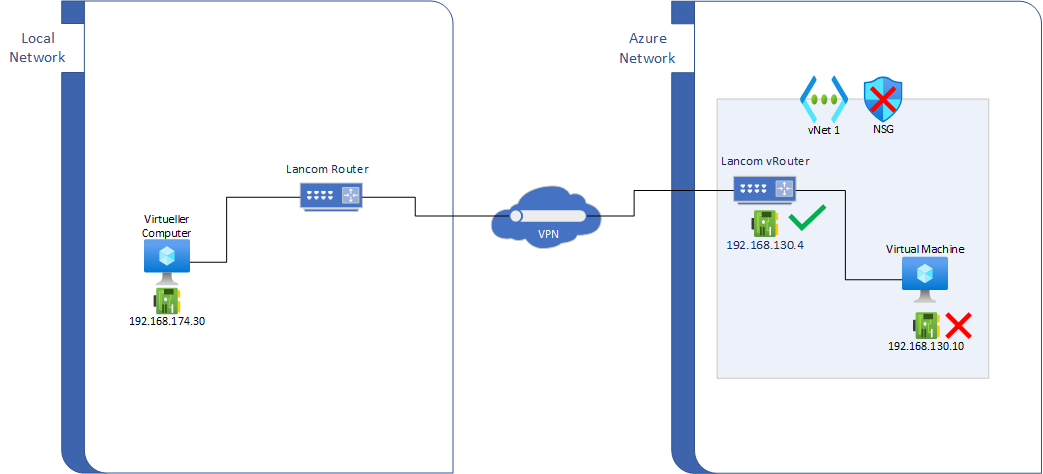
in Azure I installed a Lancom vRouter to connect our local Network with another Lancom On-Premise Router. That works fine, so I can connect the vRouter interface from local network via VPN gateway.
After that I created a virtual machine in the same virtual network in Azure. The network security group is deleted. Sadly it is not possible to connect the created virtual machine in the same virtual network.
I´m looking forward to any ideas.
Regards
Benjamin
Azure Virtual Network
4 answers
Sort by: Most helpful
-
-
SaiKishor-MSFT 17,336 Reputation points
2022-03-09T14:38:49.787+00:00 @Benjamin Laubert Thank you for sharing the Network Diagram. I see the source is a on-premise machine and you are able to reach the Lancom vRouter but not the VM(192.168.130.10) via the VPN, is that right? Please verify the following details:
- Do you have a User-defined routes (UDRs) on virtual network subnets that direct traffic to Lancom Router for the on-premise network?
- Does the NSG associated to either the Lancom vRouter or the VM allow traffic to/from the on-premise network?
- Is IP Forwarding enabled on the Lancom vRouter? If not, here is how to enable it:
Use Azure portal:
- Locate the NVA resource in the Azure portal, select Networking, and then select the Network interface.
- On the Network interface page, select IP configuration.
- Make sure that IP forwarding is enabled.
- Check whether the traffic can be routed to the Lancom Router from the VM in Azure
On Azure portal, open Network Watcher, select Next Hop.
- Specify a VM that is configured to redirect the traffic to the NVA, and a destination IP address at which to view the next hop.
- If the Lancom vRouter is not listed as the next hop, check and update the Azure route tables.
- Check whether the traffic can reach the Lancom vRouter *In Azure portal, open Network Watcher, and then select IP Flow Verify.
- Specify the VM and the IP address of the Lancom vRouter, and then check whether the traffic is blocked by any Network security groups (NSG).
- If there is an NSG rule that blocks the traffic, locate the NSG in effective security rules and then update it to allow traffic to pass. Then run IP Flow Verify again and use Connection troubleshoot to test TCP communications from VM to your internal or external IP address.*
- Check if the VM is listening on the port you are trying to connect on and that there is no Firewall etc., blocking this traffic on the VM.
Hope this helps. Please troubleshoot using the above steps and let us know once you have more details or require further assistance. Thank you!
-
 risolis 8,741 Reputation points
risolis 8,741 Reputation points2022-03-10T01:39:53.803+00:00 Thanks for the topology @Benjamin Laubert
Do you have this subnet/host IP address enable on your "Endpoint and Traffic Selectors"??
Great info as well @SaiKishor-MSFT
Cheers!!
-
Benjamin Laubert 1 Reputation point
2022-03-21T09:50:43.787+00:00 Hey @SaiKishor-MSFT and @risolis ,
sorry for the late response and many many thanks for all the informationen!
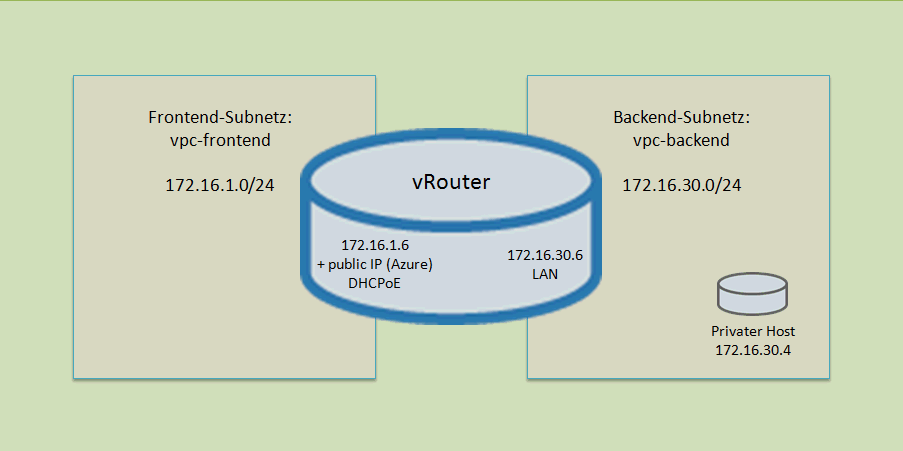
My/our final setting is near the same as you can see in the attached topology. I cutted the network into two sections.