Hi @Junaid
Limitless' answer above covers scenario 1 which you have already have configured.
It will be a little more difficult to meet all the requirements for scenario 2, but I think we can get close.
As someone else will be pre-staging the computer objects, you can change the delegation rights when the object is create to grant the second group permissions to join the computer to the domain. By creating a new group and specify that group when the computer object is created this will grant the users of the group the ability to join a computer with the same name to the domain.
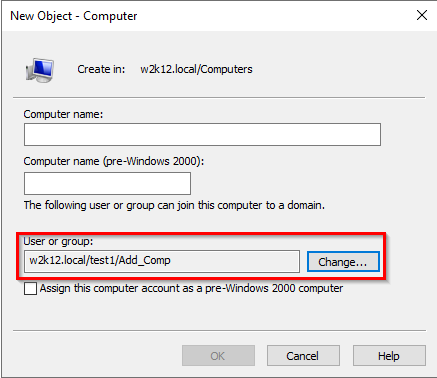
These are the rights that are assigned to the computer object
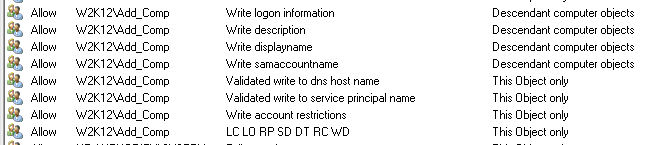
However, this method does provide the group members with the ability to delete the computer object, which fails to meet one of your requirements.
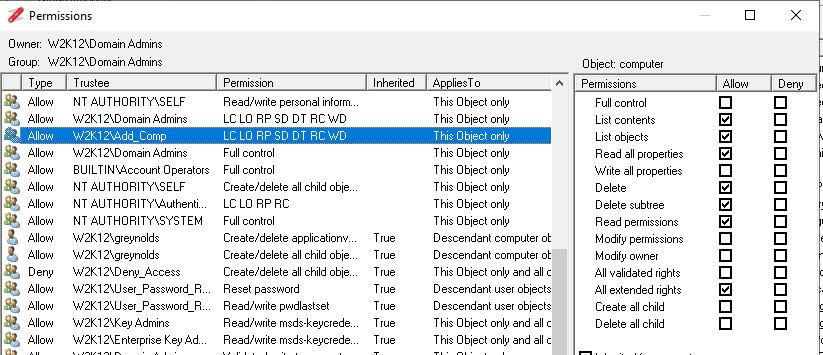
To overcome this you will need to assign the permissions manually to the OU structure that contains the computer objects. Note: By restricting these permissions you are also preventing the users from moving the computer objects to a different OU.
You will need to assign the following permissions, all of which will be inherited by descendant computer objects. I've provided these are dsacls commands as the ADUC will not allow you to configure all of these permissions via the UI:
Change "ou=domain computers,dc=w2k12,dc=local" to your OU and change add_comp to your group
dsacls "ou=domain computers,dc=w2k12,dc=local" /G "add_comp:WP;logon information;computer" /I:S
dsacls "ou=domain computers,dc=w2k12,dc=local" /G "add_comp:WP;description;computer" /I:S
dsacls "ou=domain computers,dc=w2k12,dc=local" /G "add_comp:WP;displayname;computer" /I:S
dsacls "ou=domain computers,dc=w2k12,dc=local" /G "add_comp:WP;description;computer" /I:S
dsacls "ou=domain computers,dc=w2k12,dc=local" /G "add_comp:WP;samaccountname;computer" /I:S
dsacls "ou=domain computers,dc=w2k12,dc=local" /G "add_comp:WS;Validated write to service principal name;computer" /I:S
dsacls "ou=domain computers,dc=w2k12,dc=local" /G "add_comp:WS;Validated write to dns host name;computer" /I:S
dsacls "ou=domain computers,dc=w2k12,dc=local" /G "add_comp:WP;account restrictions;computer" /I:S
dsacls "ou=domain computers,dc=w2k12,dc=local" /G "add_comp:LCLORPRC;;computer" /I:S
These are the permissions that will be assigned to OU:

The only issue I can see with these permissions, is that we have removed the rights to change the 'Permissions' of the computer objects, which might be required during the domain join to update the permissions of the object.
If the domain join fails with these permissions, then I would change the last line to 'LCLORPRCWD' and run the command again. While this change doesn't give the user the right to delete the object, it does allow them to change their rights, so they could change their permissions to allow them to delete the computer object.
If the domain join still fails with these permissions, review the netsetup.log for more details on the failure.
Gary.






