Hi,
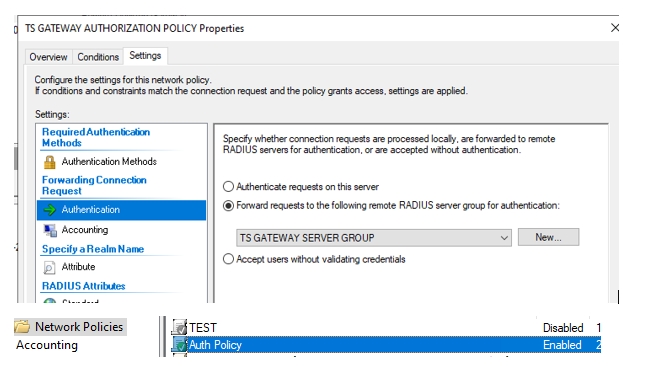
As per my previous post I have setup a fresh copy of Windows 2022 and installed only all windows updates and the NPS server role.
Set it up as per the rdg mfa guide linked above and I get the exact same issue.
The authentication works the first time as it should, but on subsequent tries nothing happens.
In the event logs on the RDS Gateway server it logs...
The remote RADIUS server IP Address has not responded to 5 consecutive requests. The server has been marked as unavailable.
On the new NPS server I do see a security event relating to the request as follows:
Event ID 6274
Network Policy Server discarded the request for a user.
Contact the Network Policy Server administrator for more information.
User:
Security ID: NULL SID
Account Name: mydomain\mytestuser
Account Domain: mydomain
Fully Qualified Account Name: mydomain\mytestuser
Client Machine:
Security ID: NULL SID
Account Name: mypc.mydomain.co.uk
Fully Qualified Account Name: mydomain\mypc$
Called Station Identifier: UserAuthType:PW
Calling Station Identifier: -
NAS:
NAS IPv4 Address: -
NAS IPv6 Address: -
NAS Identifier: -
NAS Port-Type: Virtual
NAS Port: -
RADIUS Client:
Client Friendly Name: Gateway
Client IP Address: gatewayipaddress
Authentication Details:
Connection Request Policy Name: Use Windows authentication for all users
Network Policy Name: -
Authentication Provider: Windows
Authentication Server: Win2022NPS.mydomain.co.uk
Authentication Type: -
EAP Type: -
Account Session Identifier: -
Reason Code: 10
Reason: The request was discarded because an extension dll crashed or malfunctioned.
So seems like something within the NPS files or the MFA extension not working as it should?
I am using the NPSExtnForAzureMfaIntsaller v 1.1.1892.2
Thank you,
Jamie