Hi @DaNmAN
Agree with Andy, and the official document introduces the scenario as well:
How do SPF and DMARC work together to protect email in Microsoft 365?
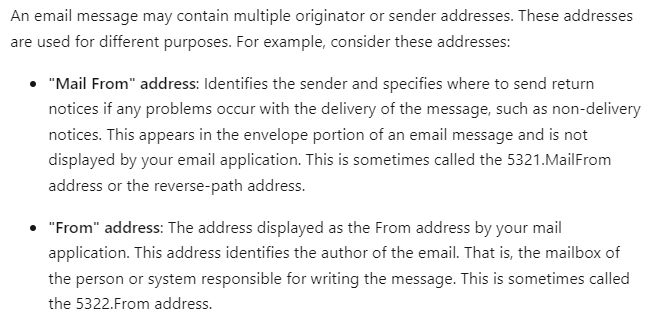
SPF uses a DNS TXT record to provide a list of authorized sending IP addresses for a given domain. Normally, SPF checks are only performed against the 5321.MailFrom address. This means that the 5322.From address is not authenticated when you use SPF by itself. This allows for a scenario where a user can receive a message, which passes an SPF check but has a spoofed 5322.From sender address.
In this transcript, the sender addresses are as follows:
Mail from address (5321.MailFrom): ******@phishing.contoso.com
From address (5322.From): ******@woodgrovebank.com
If you configured SPF, then the receiving server performs a check against the Mail from address ******@phishing.contoso.com. If the message came from a valid source for the domain phishing.contoso.com, then the SPF check passes. Since the email client only displays the From address, the user sees that this message came from ******@woodgrovebank.com. With SPF alone, the validity of woodgrovebank.com was never authenticated.
When you use DMARC, the receiving server also performs a check against the From address. In the example above, if there is a DMARC TXT record in place for woodgrovebank.com, then the check against the From address fails.
If an Answer is helpful, please click "Accept Answer" and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.

