Hi @KF ,
Thank you for your query. From your query, I understand that you are getting AADSTS500089 error when attempting to access Azure Portal using SAML 2.0 SSO with Azure AD from from a third-party IdP.
By tracking the details from the backend for your tenant based on the correlation ID and the timeframe of the error you have provided, I can see incorrect audience sent by your IDP "iss":"https://##.authpoint.cloud.watchguard.com/ACC-1####81" in the SAML token like "aud":["https://login.microsoftonline.com/812a###9-b623-####-ac35-0efdc###c5/"] , but it must be urn:federation:MicrosoftOnline. So, could you please check what value was specified in your Identity provider's identity field (aks RealmID or entityID ) in your identity provider? also would request you to validate your identity provider compatibility with Azure AD since you are using Non-Microsoft identity provider for federation with Azure AD.
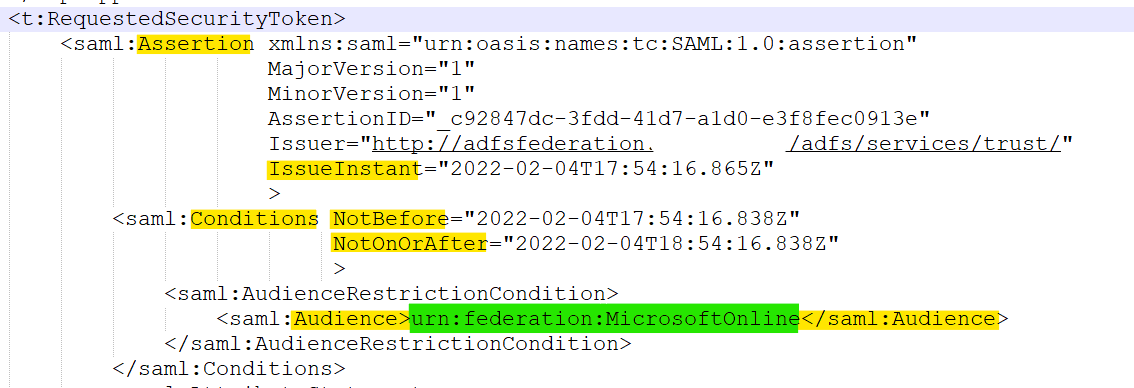
Additionally, ensure that your identity provider is sending proper values in the following fields in the token IssueInstant , NotBefore , saml:Audience as shown below. Also, make sure identity provider is using the right key algorithm for signing token like RSA. Here's sample-token.xml for reference which you can use to compare non-working token. For detailed information about compatibility, see Azure AD federation compatibility list and Azure AD identity provider compatibility docs. Hope this helps.
Hope this helps.
-----
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.

