@karthik palani , For your questions, here are my suggestions:
- To block personal device in conditional policy, we can set "deviceOwnership" Equals Personal to block.
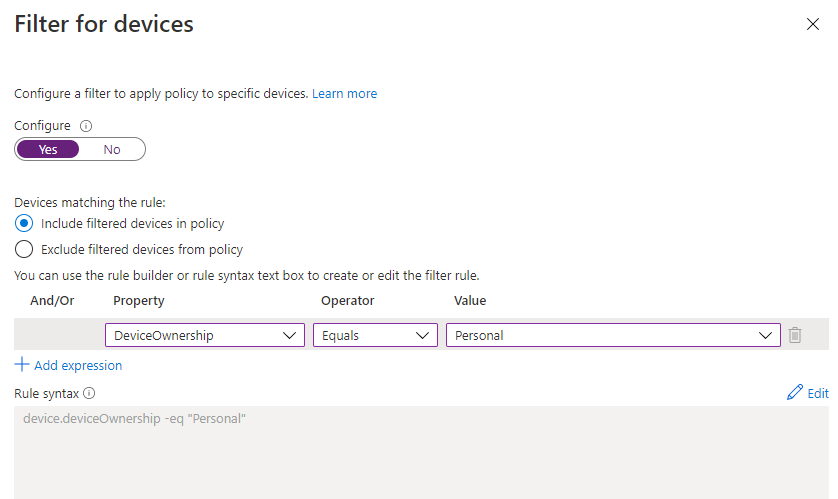
- To block network share, based on my research, there's no built policy Intune to do this. But I find maybe we can use Powershell to disable file and printer sharing to accomplish this. Here is a link for the reference:
https://www.c-sharpcorner.com/article/how-to-enable-or-disable-file-and-printer-sharing-in-windows-102/
Note: Non-Microsoft link, just for the reference.
We can test the command on device manually to see if it can work. If yes, then we can deploy Powershell Script via Intune to do it in a batch.
- For the password complexity policy, the support value is as below. Please check if our situation is met.
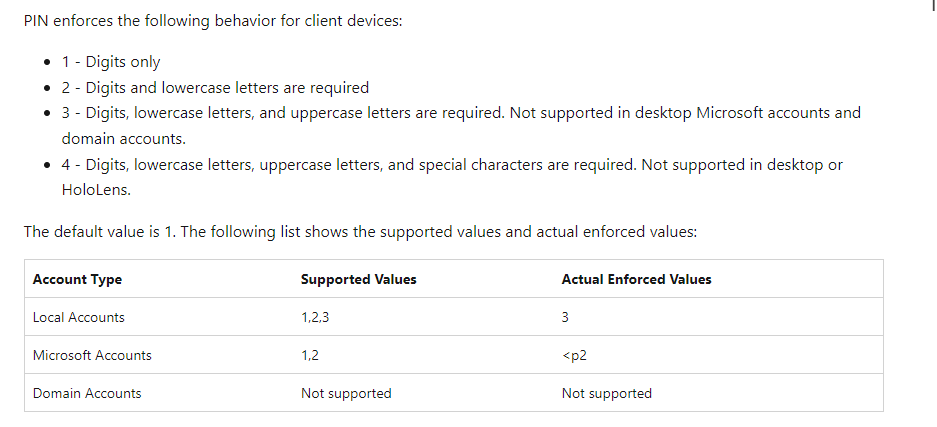
https://learn.microsoft.com/en-gb/windows/client-management/mdm/policy-csp-devicelock?WT.mc_id=Portal-fx#devicelock-mindevicepasswordcomplexcharacters
For the password threshold, to know it better, could you let us know where we configure the setting?
Please check the above information, if there's any update, feel free to let us know.
If the answer is helpful, please click "Accept Answer" and kindly upvote it. If you have extra questions about this answer, please click "Comment".
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.
