Hello @Taranjeet Malik ,
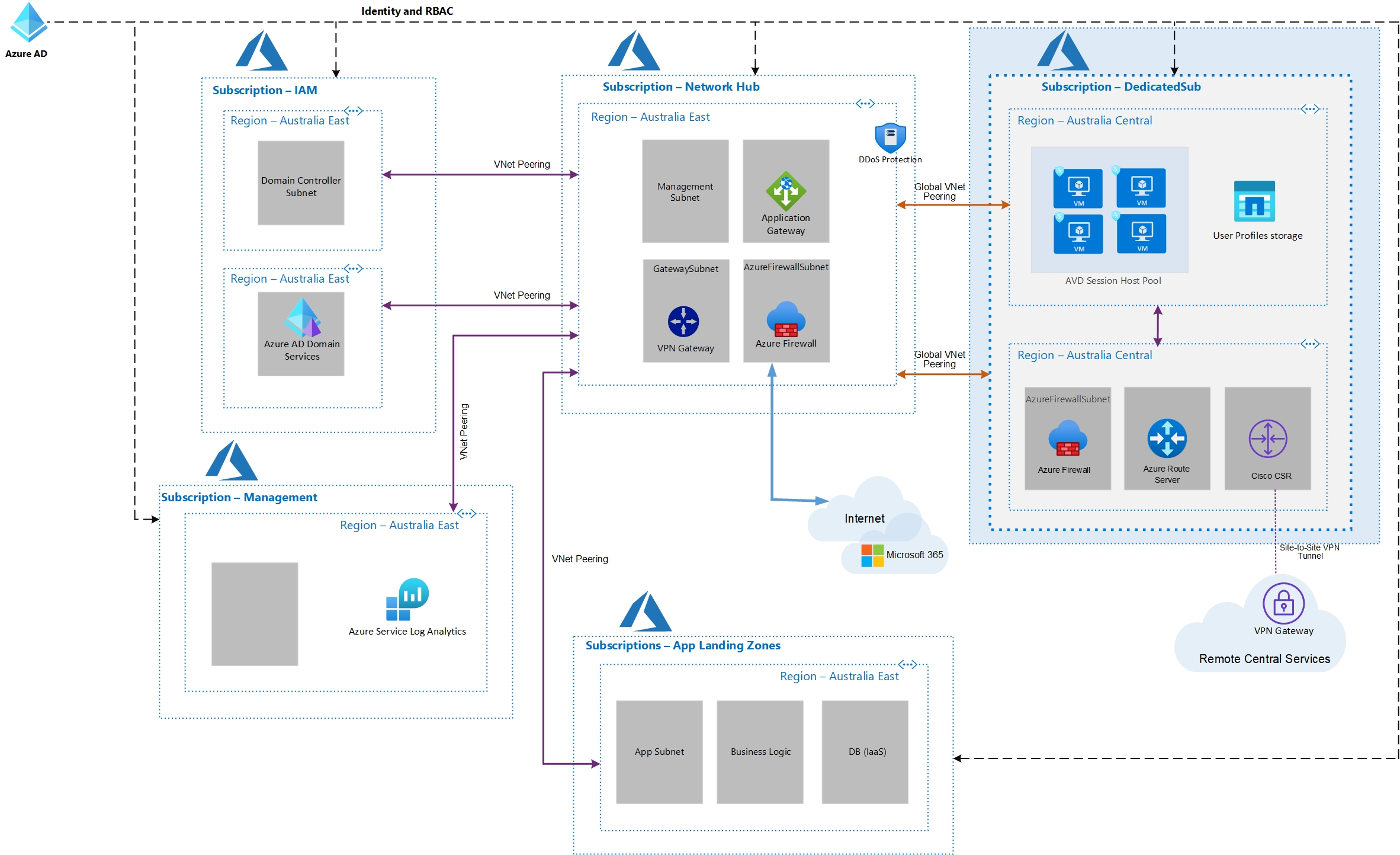
I understand that you are building an Enterprise Scale Azure landing zone as described here and would like to ensure that this architecture works.
Your shared architecture should work just fine. As it is one of the recommended enterprise-scale architecture implementation.
Refer : https://learn.microsoft.com/en-us/azure/cloud-adoption-framework/ready/enterprise-scale/implementation
Azure Virtual Desktop (AVD) solution running in the DedicatedSub subscription within a separate VNet needs to connect to Azure AD DS instances in the IAM subscription.
Yes, this will work. If you are able to communicate to the Azure AD DS using Vnet peering/VPN, you will be able to join the Azure AD DS domain using your Azure AD credentials.
Refer : https://learn.microsoft.com/en-us/azure/architecture/example-scenario/wvd/windows-virtual-desktop
Logs (for services like Azure Firewall, AVD) from the DedicatedSub needs to be sent to Log Analytics Workspace in the Management subscription.
It will work without any issues as long as you have Vnet peering connectivity and appropriate privileges or access.
Refer : https://learn.microsoft.com/en-us/azure/network-watcher/traffic-analytics-faq#can-my-azure-storage-account-be-in-one-subscription-and-my-log-analytics-workspace-be-in-a-different-subscription-
Kindly let us know if the above helps or you need further assistance on this issue.
----------------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.