Hey Dev073, thanks for getting back to me on this issue.
I am signing in to me Win 10 21/H2 laptop using Windows Hello PIN auth - which I understand is considered a strong authentication method.
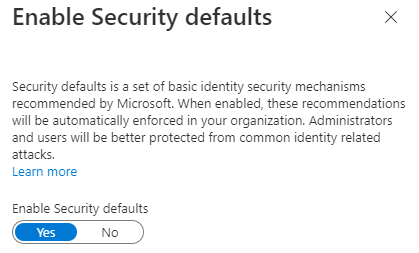
I can't remove the MFA requirement for my user account as it is the account that I use as Global Admin for my tenant and also when logging in to Azure portal - On the free Azure AD Tenant, both of these force MFA which can't be turned off.
If I create another user account in Azure AD to use as the login account for the Azure VM, I have to first try and login to the portal with this user account to reset the initial password, before I can login to the Azure VM with it. At this point, as I have tried to login to the Azure Portal with the account, then it sets a timer of 14 days until it will enforce MFA. The account works in the short-term for logging in to the Azure VM, but I presume this will stop working in 14 days.
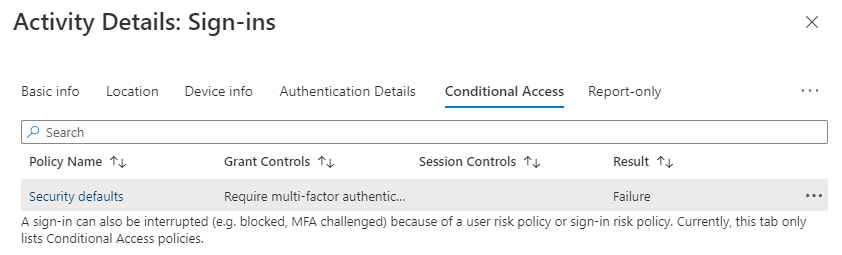
When I look at the Azure User's sign-in logs, you can see that the Windows Sign-In shows as successful:

But it is the pass-through authentication that is sent to the Azure VM's Windows OS that then fails to login to the Windows session on the VM:
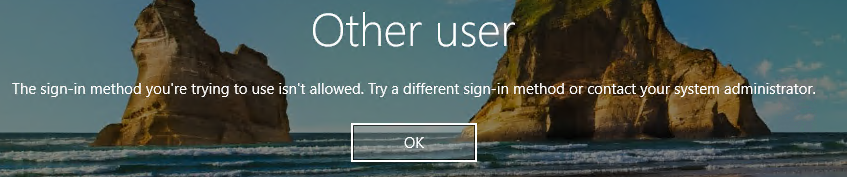
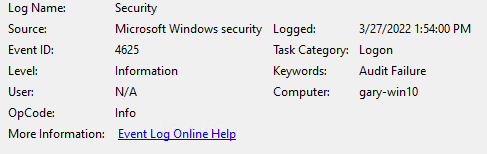
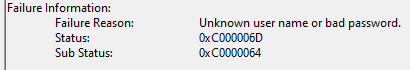
When I look at the security logs on the VM, all I see is a Windows 4625 error which does not give me much of a clue as to why it did not allow the login: