Ok, now I understand why it's not working.
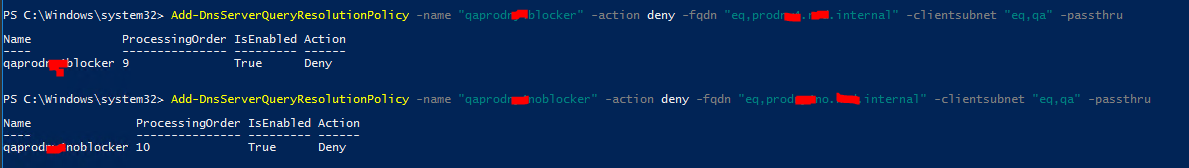
The Add-DnsServerQueryPolicy command is used to configure a set of matching rules or criteria, these criteria are then checked against the incoming DNS queries, if all the criteria match, then the action is applied.
For your policy, I think you are looking for this, please correct if this is wrong:
- Machines are in the newdev ip address range, that try to resolve *.dev.abc.internal block the query
These are the commands that you need to enter:
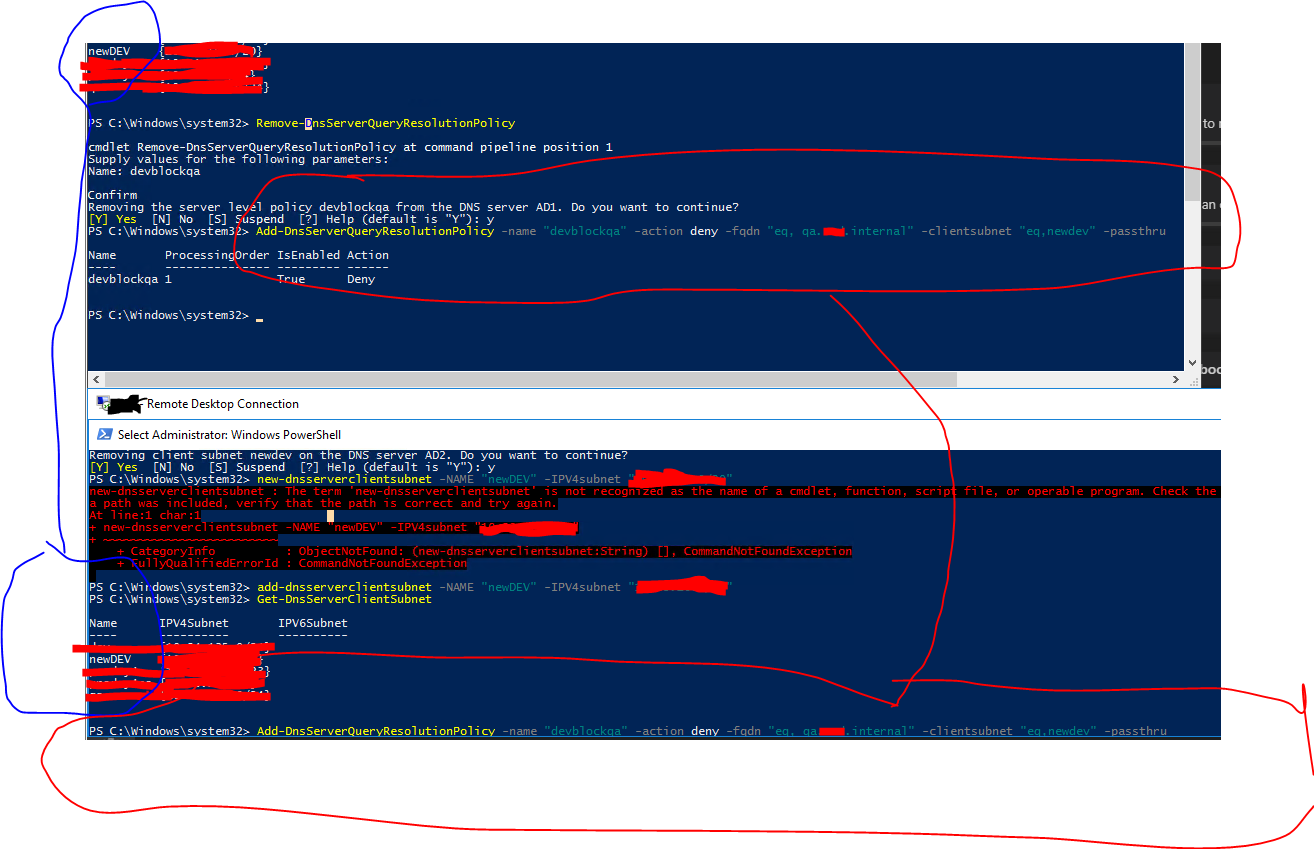
Add-DnsServerClientSubnet -name NewDev -ipv4subnet 192.168.1.0/24
This defines the IP address range of the machines that you want to block from accessing the dev.abc.internal domain. As I mentioned in your other post, there is no method to check if a machine is registered to a specific DNS domain, IP address is the only option to filter at a machine level.
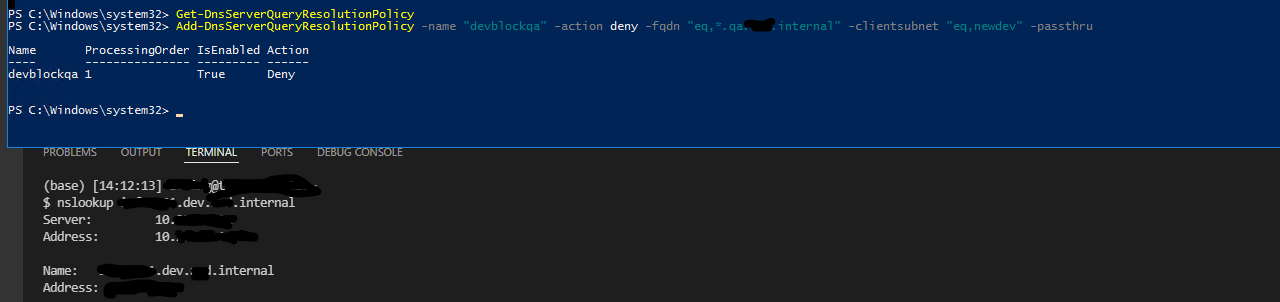
Add-DnsServerQueryResolutionPolicy -name prodblock -action deny -fqdn "EQ,*.dev.*abc*.internal" -ClientSubnet "EQ,NewDev"
This policy will check any incoming query that are for the dev.abc.internal domain, including any entry or subdomains, and the client machine has an IP address in the NewDev IP address range then the query will be blocked. If the FDQN parameter doesn't include a wildcard, only the specified FQDN will be blocked. So to block all entries in a domain, the FQDN parameter would be *.dev.abc.internal.
The configuration of the DNS policies is very clunky and some sort of verification cmdlet would be useful. I have thought about creating a tool to do this, as my limited playing with the DNS policy has highlighted how painful this is.
Gary.