Hello @Jason Leidy ,
Thank you for posting here.
After reading several times , here are the answers for your references.
Q1:What happens when I install the August patch on all of my clients (all Windows 10 1909) and servers.
A1:We only need to install the August patch on all DCs in the forest.
All will happen below after you install the August patch on all DCs in the forest.
1.After deploying the August 11th updates to all DCs (including Windows DCs (including read-only domain controllers) and non-Windows DCs) in the forest.
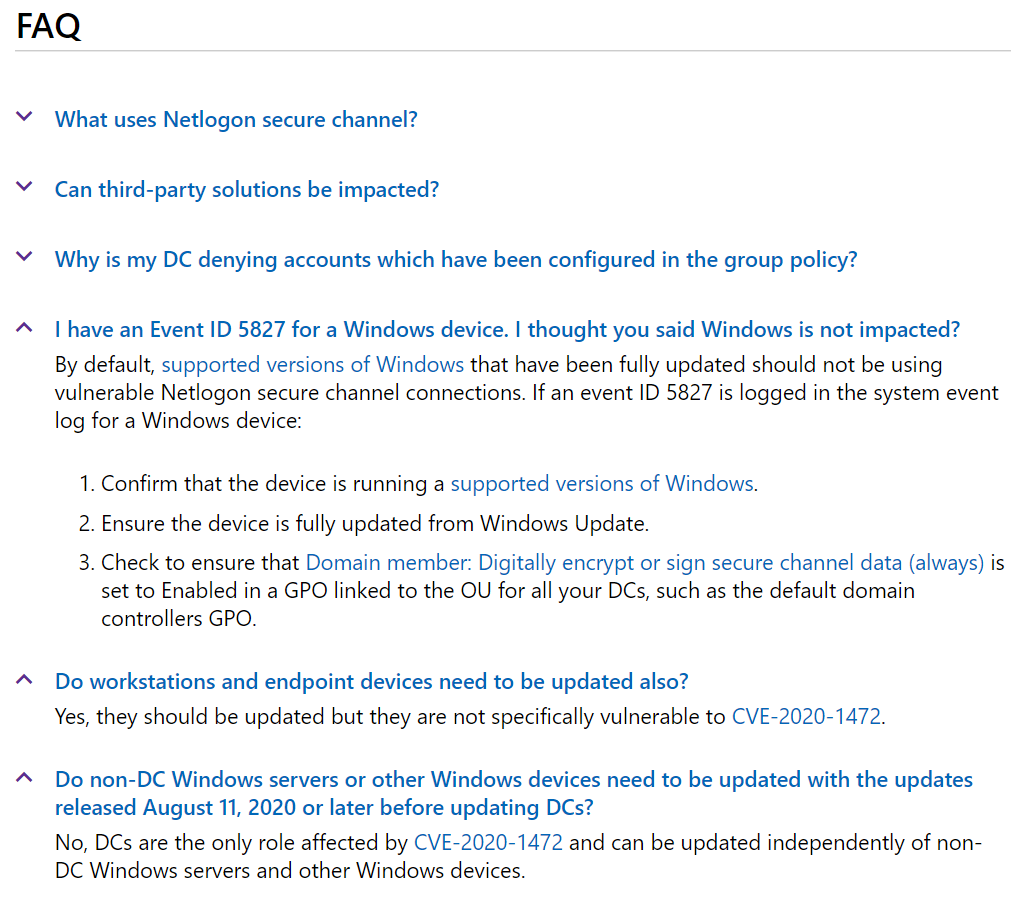
2.By default, supported versions of Windows that have been fully updated should not be using vulnerable Netlogon secure channel connections.
3.Detecting non-compliant devices using event ID 5829.
3-1 Monitor patched DCs for event ID 5829 events.
3-2 The event ID 5829 determines which devices in your environment are using vulnerable Netlogon secure channel connections (referred to as non-compliant devices in that article).
3-3 The events will include relevant information for identifying the non-compliant devices.
4.To find non-compliant devices (A non-compliant device is one that uses a vulnerable Netlogon secure channel connection.) in advanve from event ID 5829 on all DCs before we install February 9, 2021 updates.
4-1 Deploying the August 11th updates to all DCs
4-2 Monitor patched DCs for event ID 5829 events. Event ID 5829 is generated when a vulnerable connection is allowed during the initial deployment phase.
4-3 To resolve the vulnerable Netlogon secure channel connections(enforce secure RPC when using the Netlogon secure channel ), move to enforcement mode in advance of the February 2021 enforcement phase
Method 1
Set Registry on all DCs.
Registry subkey: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters
Value: FullSecureChannelProtection
Data type: REG_DWORD
Value:1 – This enables enforcement mode.
DCs will deny vulnerable Netlogon secure channel connections unless the account is allowed by the Create Vulnerable Connection list in the "Domain controller: Allow vulnerable Netlogon secure channel connections" group policy.
Method 2
Wait for February 9, 2021 updates
Q2:Non-compliant machines won't be able to get logged on?
A2:If we only install August 11, 2020 updates, non-compliant machines will be able to get logged on. Event ID 5829 is generated when a vulnerable connection is allowed during the initial deployment phase. These connections will be denied when DCs are in enforcement mode.
Q3:I don't know which devices are non-compliant (not using secure RPC when using the Netlogon secure channel).
A3:To find non-compliant devices in advanve after August 11, 2020 updates before we install February 9, 2021 updates.
1 Deploying the August 11th updates to all DCs.
2 Monitor patched DCs for event ID 5829.
Q4:How is that different than what the February update does.
A4:
August 11, 2020 updates - Initial Deployment Phase
We can find non-compliant machines in advance from event ID 5829 on all DCs before we install February 9, 2021 updates.
February 9, 2021 updates - Enforcement Phase (make FullSecureChannelProtection=1 on all DCs forcely)
If we actually find some non-compliant devices and we want "the Netlogon service allow vulnerable Netlogon secure channel connection from a machine account", we should set "Domain controller: Allow vulnerable Netlogon secure channel connections" group policy for Domain Controllers.
Domain controller: Allow vulnerable Netlogon secure channel connections ==> Allow: The domain controller will allow the specified group/accounts to use a Netlogon secure channel without secure RPC.
After that, we may receive Event ID 5830 and Event ID 5831.
Event ID 5830 will be logged when a vulnerable Netlogon secure channel machine account connection is allowed by "Domain controller: Allow vulnerable Netlogon secure channel connections" group policy.
Event ID 5831 will be logged when a vulnerable Netlogon secure channel trust account connection is allowed by "Domain controller: Allow vulnerable Netlogon secure channel connections" group policy.
Otherwise, we actually find some non-compliant devices, and we want "the Netlogon service deny vulnerable Netlogon secure channel connection from a machine account" and we does not set "Domain controller: Allow vulnerable Netlogon secure channel connections" group policy for Domain Controllers, we may receive Event ID 5827 and Event ID 5828.
Event ID 5827 will be logged when a vulnerable Netlogon secure channel connection from a machine account is denied.
Event ID 5828 will be logged when a vulnerable Netlogon secure channel connection from a trust account is denied.
Hope the information above is helpful. If anything is unclear, please feel free to let un know.
Best Regards,
Daisy Zhou