I'm using Azure AD provisioning for Dropbox and it works fine with the exception of those users that have multiple proxy addresses where the primary domain email address isn't being used. Instead they are using a secondary address as their primary from one of our alias domains that we manage.
An example would be a better way to explain this:
Username: jdoe
Primary domain is domain1.com
Alias domain is domain2.com
In Active Directory when creating a user our primary domain is used by default. We also have users using our alias domain as their primary SMTP email address in AD. When you look at their proxyAddresses attribute in AD you see:
SMTP:@domain2.com
smtp:@domain1.com
We've used Dropbox before, so username jdoe already has an account that uses ******@domain2.com but now that I'm using Azure AD for provisioning to Dropbox it imported their account as ******@domain1.com because it's going by what our primary default domain is.
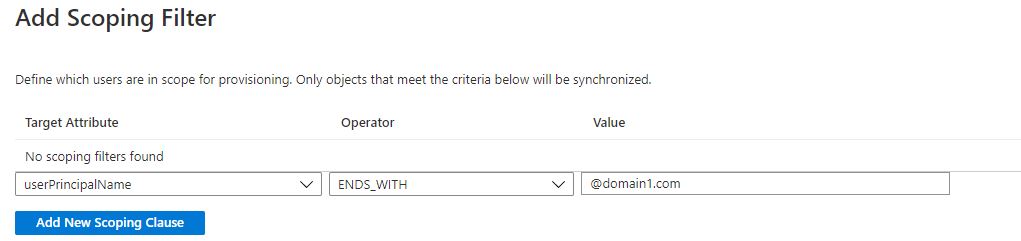
I'm looking for a way where I can use scoping filters or editing existing mapping attributes to where an existing user like jdoe doesn't get a second account imported by provisioning when he's already in Dropbox as a member using our alias domain