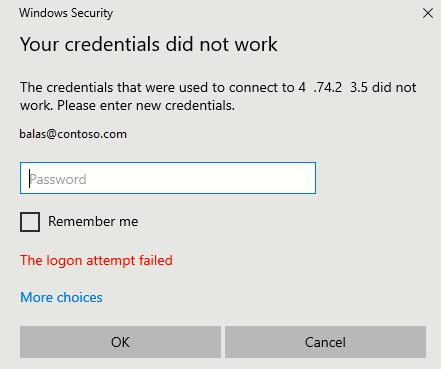
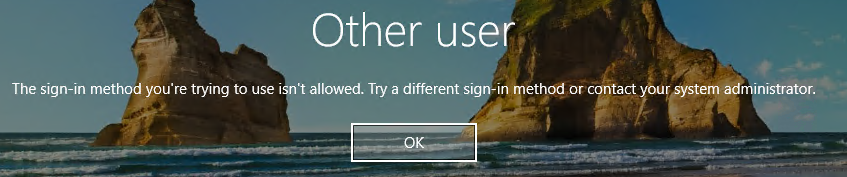
I have an Azure AD Tenant (Free) and I have connected an Azure VM (Win10 Pro 21/H2) to it, but find that I cannot login to it via RDP with any Azure AD user accounts (with VM Administrator/User RBAC roles) from my home Win10 machine that is also connected to the Azure AD Tenant.
The user account on the Windows 10 Pro 21/H2 home machine has Windows Hello and a PIN set - which I believe is considered a Strong Authentication mechanism wrt MFA.
If I have "Security Defaults" enabled on my Azure AD tenant, my users cannot login, whereas if I set it to disabled - then they can login - I suspect that this is due to "Security Defaults" forcing MFA for my users (which I want), but that the Windows login is not able to accept the MFA login (but I thought it should if the client endpoint has Strong Auth / Windows Hello & PIN).
I want to have "Security Defaults" Enabled for security reasons, but also want to be able to RDP to my Azure VM's - how can I do this?