Hello @CrestApps
Please check if managed identity is assigned to the web app deployment slot.
az webapp identity show --name MyWebapp --resource-group MyResourceGroup --slot MySlot
az webapp config container show --name MyWebapp --resource-group MyResourceGroup --slot MySlot
https://github.com/Azure/azure-powershell/issues/13109
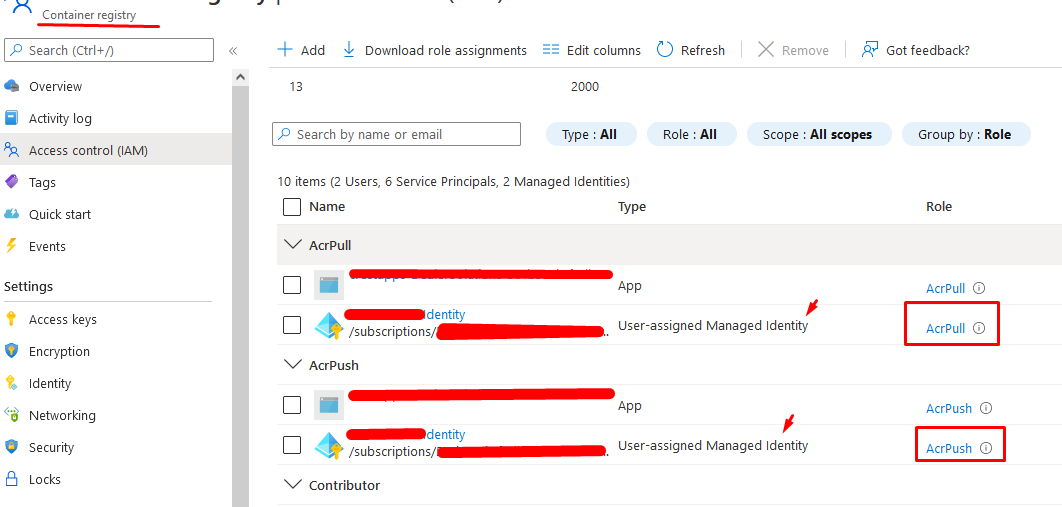
Assign an identity to your WebApp Slot where ID_Name is the name of your UserIdentity which you can find in Enterprise Apps
# Modify for your environment
Identity_ARMID=$(az identity show -g $RG_Name -n $ID_Name --query id -o tsv)
Webapp_Config=$(az webapp show -g $RG_Name -n $Web_Name --query id --output tsv)"/config/web"
ClientID=$(az identity show -g $RG_Name -n $ID_Name --query clientId --output tsv)
#Assign managed-identity to webapp
az webapp identity assign -g $RG_Name -n $Web_Name --identities $Identity_ARMID --slot MySlot -o none
#Configure WebApp to use the Manage Identity Credentials to perform docker pull operations
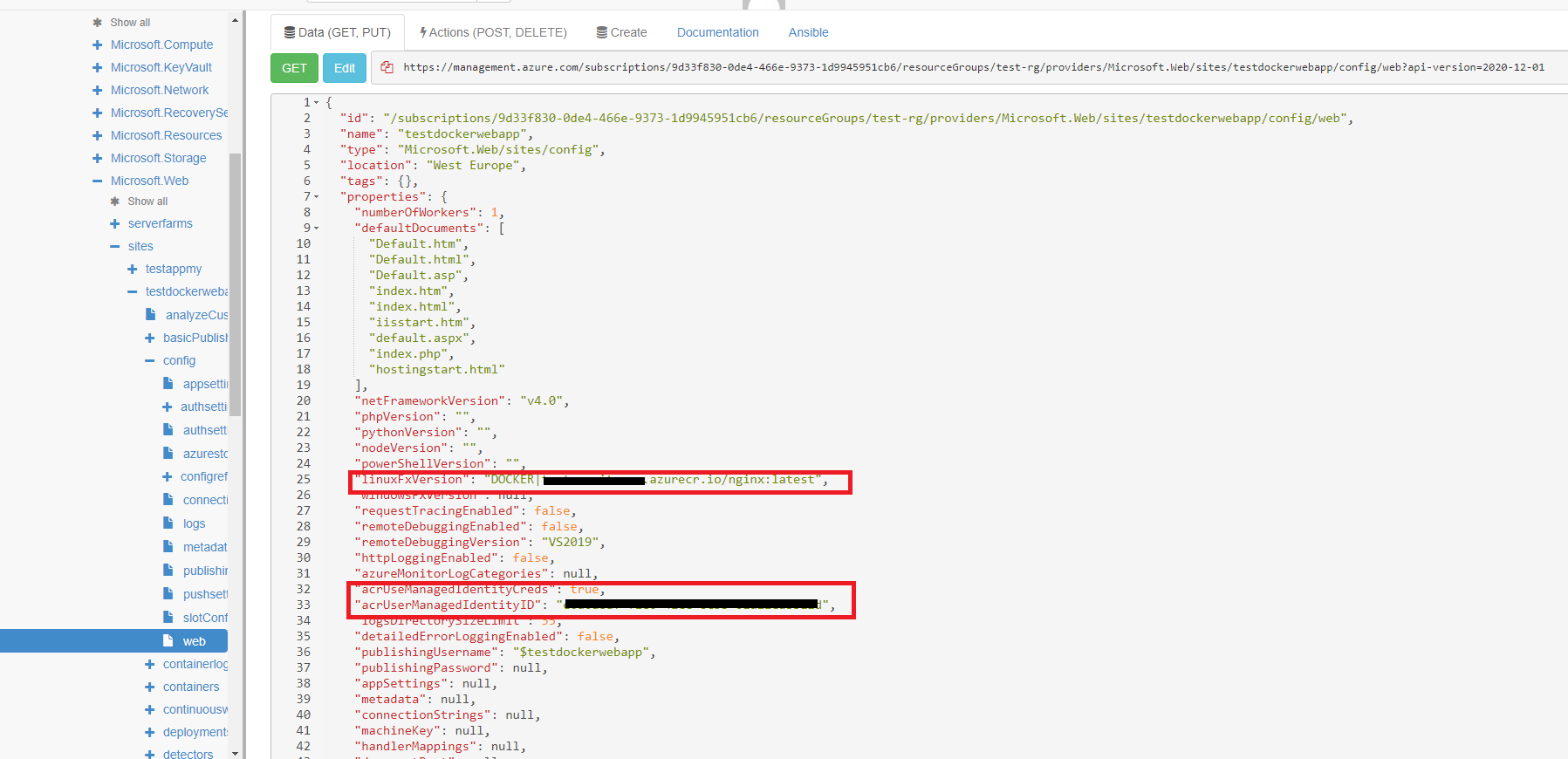
az resource update --ids $Webapp_Config --set properties.acrUseManagedIdentityCreds=True -o none
az resource update --ids $Webapp_Config --set properties.AcrUserManagedIdentityID=$ClientID -o none
Configure WebApp to pull image:tag from ACR
# Modify for your environment
ACR_URL=$(az acr show -g $RG_Name --n $ACR_Name --query privateregistry --output tsv)
Image="privateimage:152"
FX_Version="Docker|"$ACR_URL"/"$Image
#Configure the ACR, Image and Tag to pull
az resource update --ids $Webapp_Config --set properties.linuxFxVersion=$FX_Version -o none --force-string