I realize this question is old, but I thought it might be helpful to answer for any future people as it's the top ranking search result on this question.
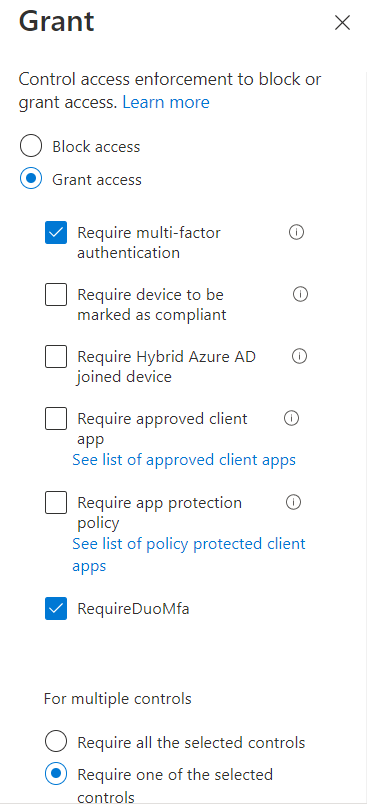
The reason that the OR condition ("Require one of the selected controls") does not work for CA policies with both Azure AD MFA and Duo MFA is due to how the conditional access policy processes the signals. It has no knowledge of which users are Duo users and which users are Azure AD MFA users so it initiates the flow for both checks.
Now with the OR condition it is still possible that only one of the checks needs to pass for the policy to grant access, but it is going to be a poor user experience regardless. Users who are only enrolled in Duo MFA would still be guided through the proof-up process to register Microsoft Authenticator while simultaneously getting Duo prompts.
The proper solution is to use two separate policies -- one targeting all users and excluding Duo MFA users and one only targeting Duo MFA users (or the inverse, using an AAD MFA group). It is important to use one group included in the first policy and excluded from a second all users policy to ensure that all users are always covered by at least one MFA policy. If you define one policy targeting Duo MFA users and another targeting AAD MFA users, you open up the possibility that somebody does not belong to either group and is not protected by MFA at all.