AdamRiddick-5896, Thanks for posting this good question.
I'm not sure if you have checked this doc Root CA on App Service already.
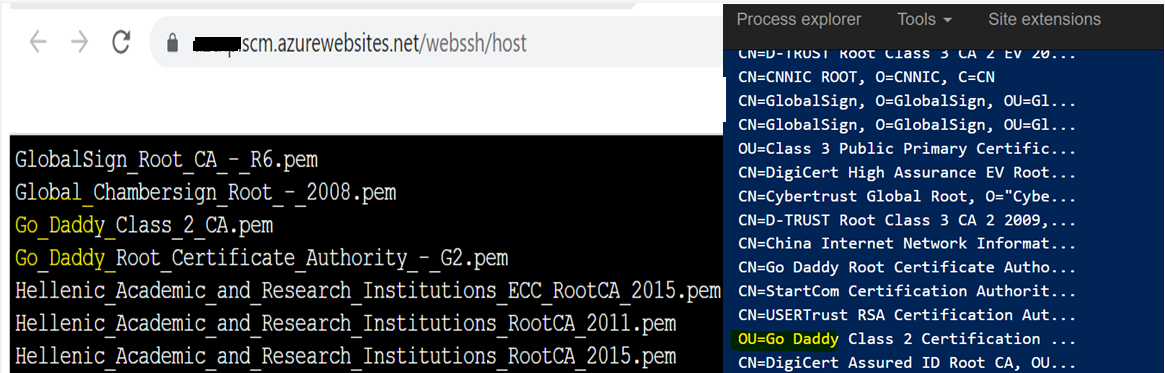
Just to highlight, App Service has a list of Trusted Root Certificates which you cannot modify in the multi-tenant variant version of App Service (as in your case), but you can load your own CA certificate in the Trusted Root Store in an App Service Environment (ASE), which is a single-tenant environment in App Service.
--(The Free, Basic, Standard, and Premium App Service Plans are all multi-tenant, and the Isolated Plans are single-tenant.)
Yes, as you mentioned, when an app hosted on Azure App Service, tries to connect to a remote endpoint over SSL, it is important that the certificate on remote endpoint service is issued by a Trusted Root CA.
So, in this case - There are two solutions (as mentioned in the doc'):
1.Use a certificate that is issued by one of the Trusted Root Certificate Authorities in App Service on the remote server.
2.If the remote service endpoint certificate could not be changed, host your app on an App Service Environment (ASE) and load your own CA certificate in the Trusted Root Store
Kindly let us know, I'll follow-up with you further. Thanks for your patience!