Hi @Rohit Mitra ,
Thanks for reaching out to Microsoft QnA.
To implement your solution in Azure, you need to deploy a DNS forwarder (server) in Azure virtual network, that will forward or query the Azure managed DNS for name resolution.
Also, since you are using a P2S VPN connection, I assume you are using Azure VPN client. I implemented this in my lab.
What I did was, deployed a VPN Gateway in the Vnet, created two subnets in the Vnet, in each subnet deployed one VM.
VM name : VM1-subnet1
Subnet : subnet1
VM name : VM2-subnet2
Subnet : subnet2
Follow the steps mentioned below:
Step 1: Install Azure VPN Client from Microsoft Store.
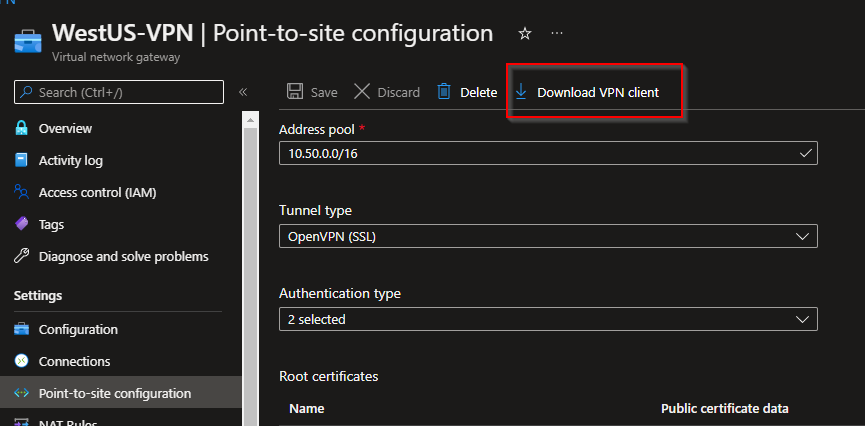
Step 2: Downloaded the VPN Client present under Point-to-site configuration of the Virtual Network Gateway blade.
Step 3: Open the downloaded VPN client folder, and open the azurevpnconfig_aad.xml file in editor.
Step 4: Install DNS role in any one of the windows server VM (I did on VM1-subnet1), open the DNS Manager, add a Conditional Forwarder. Name it internal.coudapp.net, add IP 168.63.129.16
Step 5: Open azurevpnconfig_aad.xml and add the following
<AzVpnProfile>
<clientconfig>
<dnssuffixes>
<dnssuffix>.internal.cloudapp.net</dnssuffix>
</dnssuffixes>
<dnsservers>
<dnsserver>10.1.3.4</dnsserver>
</dnsservers>
</clientconfig>
</AzVpnProfile>
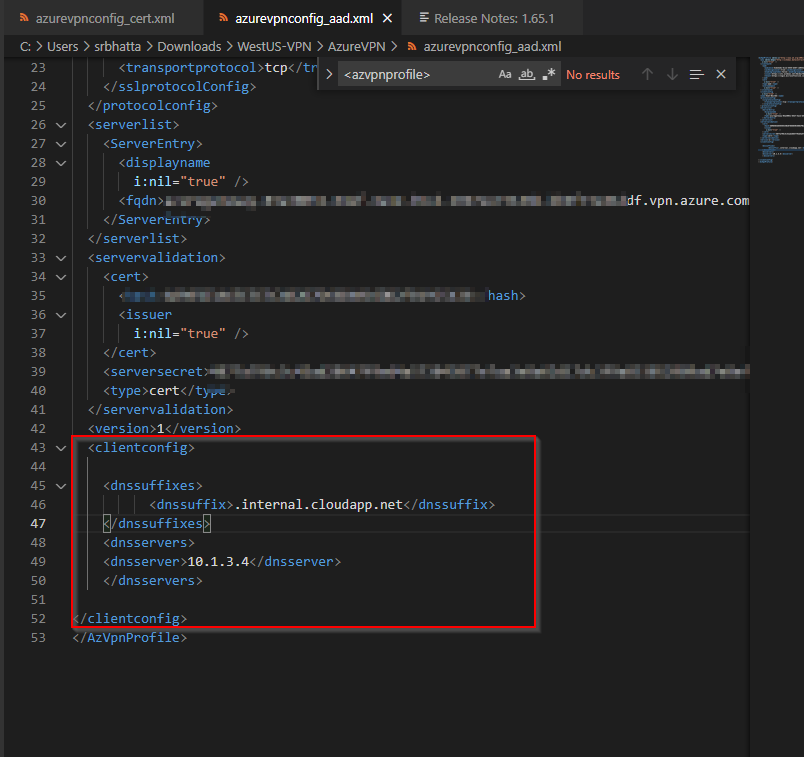
Step 6: Add your server private IP under <dnsserver> tag
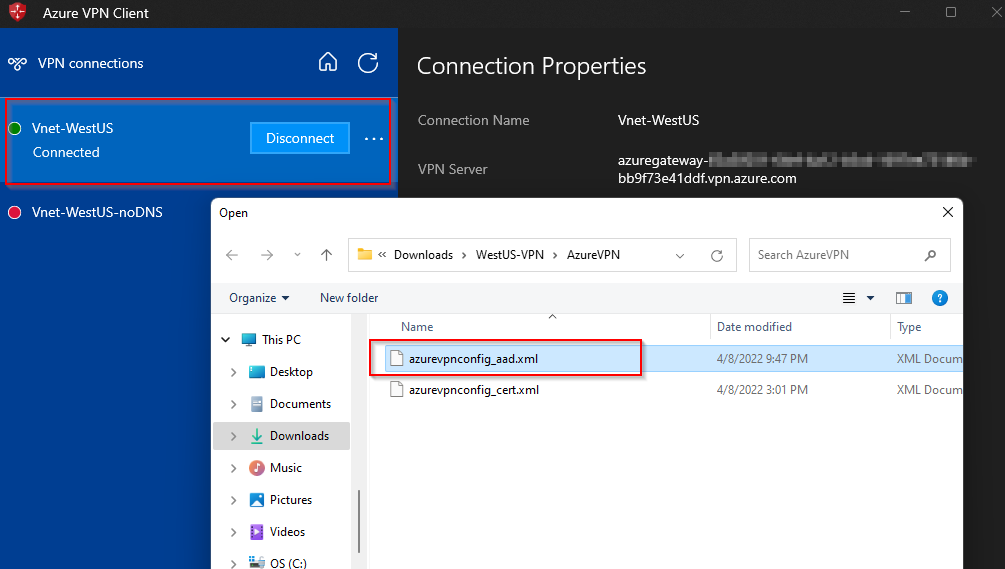
Step 7: Once again open the Azure VPN Client and select Import, then select azurevpnconfig_aad.xml file. The VPN connectivity will get re-established.
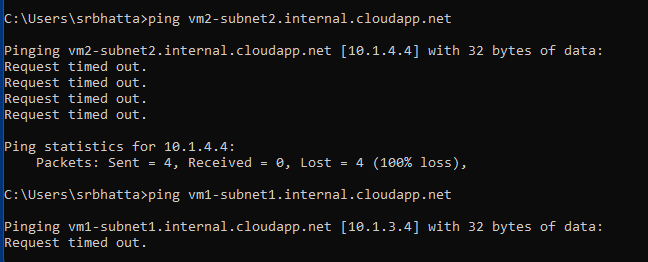
Post doing this, open the RDP prompt, and type in the vmname.internal.cloudapp.net , it will resolve to the correct IP, you can even try doing a ping to vmname.internal.cloudapp.net, and you will see the ping timing out, but you will definitely see the DNS resolution happening.
Ping test from my local machine :
------------------------------------
Please don't forget to  and
and  if you think the information provided was useful so that it can help others in the community looking for help on similar issues.
if you think the information provided was useful so that it can help others in the community looking for help on similar issues.