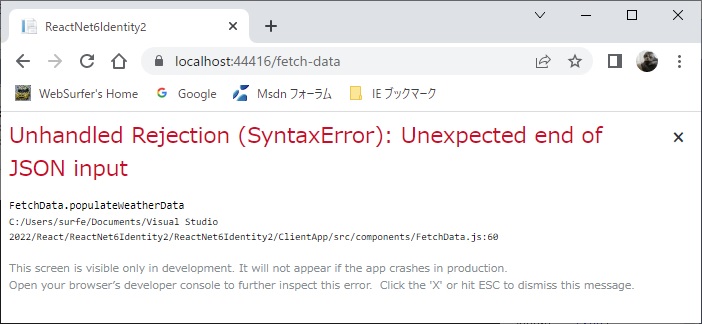
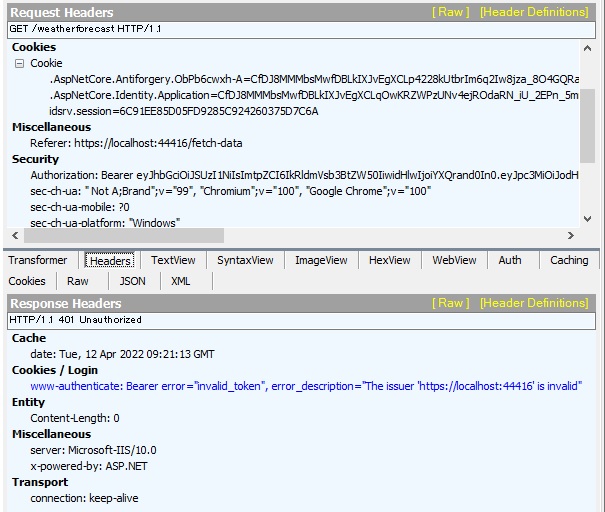
The default template works fine for me. I added a self signed cert, and trusted it for ssl. Used the default web pack proxy (react-scripts 4.3) and setupProxy.js to the asp.net core webapi.
web pack proxy: port 44421
AspNet core port: 7090
browser: https://localhost:44421
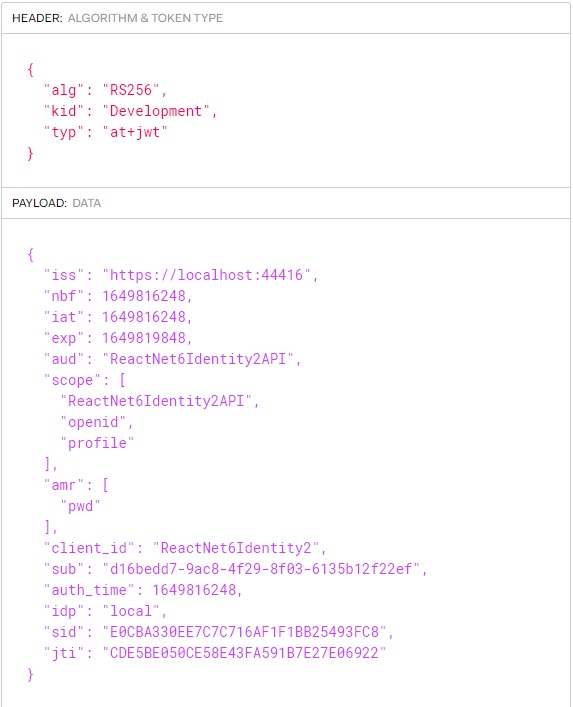
jwt token (note issuer is proxy url because of the proxy forward headers):
{
"alg": "RS256",
"kid": "Development",
"typ": "at+jwt"
}.{
"iss": "https://localhost:44421",
"nbf": 1649783616,
"iat": 1649783616,
"exp": 1649787216,
"aud": "reactauthAPI",
"scope": [
"reactauthAPI",
"openid",
"profile"
],
"amr": [
"pwd"
],
"client_id": "reactauth",
"sub": "e9ad3388-a226-40bc-b3b2-f69a1d64334a",
"auth_time": 1649783611,
"idp": "local",
"sid": "1559416FF23843827EE6EE021BAD7AC7",
"jti": "4CAE63B7538B72E03F67CE018A14D9B1"
}.[Signature]
note: I used MacOs Monterey with M1 chip and Safari