Hi
You may try like this:
Please make a copy of the config file before making any change.
1.On the SSRS server, find the RSResportServer.config file.
2.Find the<Render> tag.
3.Add the attached code inside the <Render> tags.
<Extension Name="PIPE" Type="Microsoft.ReportingServices.Rendering.DataRenderer.CsvReport,Microsoft.ReportingServices.DataRendering">
<OverrideNames>
<Name Language="en-US">CSV (Pipe delimited)</Name>
</OverrideNames>
<Configuration>
<DeviceInfo>
<FieldDelimiter>,'</FieldDelimiter>
<FileExtension>csv</FileExtension>
</DeviceInfo>
</Configuration>
</Extension>
4.Restart the SSRS
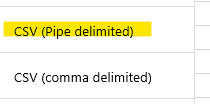
When you want to export a report to CSV format,choose the CSV (Pipe delimited).
Hope this helps!
If you have any question, please feel free to let me know.
If your problem has been solved, please mark "accepted answer" on my reply, thank you for your understanding.
Regards,
Zoe
