
I'm wondering if I have posted this question in the wrong forum or given the incorrect tagging, as I have not received any response or further questions or suggestions. I could not select any existing tag for pki, so selected something similar.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
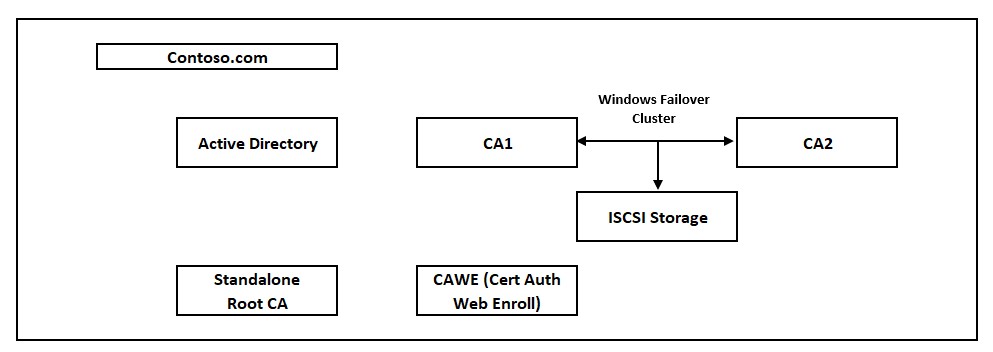
Setup: There are 2 CA Servers hosted on a Windows Failover Cluster having a shared storage, disks of which have been provided by ISCSI Storage. There is a separate CA Web Enrollment Server. IIS is installed on CA Servers for PKI. The Root CA is "Standalone Root CA".
Observation: There are 2 Certs on Ent_CA-Properties; The 1st Cert expired after 1 year and the second Cert's expiry is 5 Years, which is going to expire very soon. From one of the documents created by the old admin, we found that he renewed the cert with new key pair.
Issue: Now when we are trying to generate the CSR for Ent_CA, we are not getting the REQ file being generated.
When we enable debugging we found that the error points to the first certificate saying it is not within the time period etc. Basically it is not going past the 1st Cert.
If we try to renew the Cert with a new Key Pair we will get a REQ File but the problem is we can no longer use that option because we have recently Issued Smart Cards to users around 2-3 years before.
How to remove the Expired Cert from CA_Properties? Technically is it possible to remove Cert, Yes or NO? Some Articles say that it is not advisable to remove that old cert because CRL has that information in building the chain. For my understanding I want to know how to remove the expired cert from ENt_CA Properties.
The Microsoft Guy crashed the server while troubleshooting and we somehow managed to bring up the server.
How can we verify CRL Chain and see if everything is all right?
Under PKIVIEW.msc we see lot of Certs under NT Auth and don't exactly know why there are multiple certs expiring on the same date for the Ent_CA. Under Registry of CA Server, we see hash of two certs only, 1 is expired cert's and the other one is current Cert's hash.
Is there any powershell script which tests the health of the PKI and CRL and point us what exactly has been done wrong.
I'm wondering if I have posted this question in the wrong forum or given the incorrect tagging, as I have not received any response or further questions or suggestions. I could not select any existing tag for pki, so selected something similar.

Posting as answer, because comments do not allow long responses, all quotes are based on OP comments:
why did Microsoft Tech (Severity A case) couldn't solve the case
I don't know, I don't work for Microsoft.
Only when I enabled the debugging, i read in the logs that the certificate is not within it's validity period error and it was pointing the Thumbprint of the expired cert.
in fact, it is normal behavior. When CA starts, it validates all its installed certificates and log into event viewer if any of them is not valid. However it doesn't mean that any action is required. CA will always sign its own renewal requests only using the most recent CA certificate, which is valid (as per your information). This means that your CA has a valid cert to sign the renewal request.
simple example is, if you remove the old certificate hash from the registry key then adcs service won't start.
that's right. And that's why I said that this operation is not supported by Microsoft, because there are hidden dependencies in CA database and there is no option to manage them. And having expired previous CA certs is not a problem. Here is one of my production CAs:
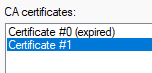
First certificate is expired, but it doesn't add any problems, because latest cert is ok.
I even spoke to MS Tech saying why don't we renew with new key pair, he didn't advise to do so because of smart cards.
they fooled you, unfortunately. I always against renewing CA cert with existing key pair, because it leads to ambiguous chains, when leaf cert's chain can be bound to older (expired) or newer (valid) root CA certs and chaining engine sometimes choose wrong chain and invalidate the certificate. Few proofs:
and this is the reason why I always recommend to renew with new key pair. New key pair results in an unambiguous single possible chain.
What I think is, the previous admin had generated many certs for the same name and not sure if each time he used new key pair or old key pair.
it is easy to track by analyzing "CA Version" extension of each CA certificate. If both numbers around the dot match, then new key pair was generated, if left-hand number is greater, then existing key pair was used.
Basically, you do not have a big problem since you are able to get renewal request for CA certificate. What you need to do is to submit request to parent CA, issue the certificate and install it on your CA. Since you have CA cluster, certificate must be installed on both nodes. This requires a little bit more frictions: when you install CA certificate to active node, backup CA certificates (using Backup CA option and choose only CA cert, without DB) and export CA certs in PFX format. Then import PFX on passive node. On a wizard page where you provide password to PFX check the option to mark private keys as exportable. It is essential part for CA certificate backup option.