Hi @senthilnathanjegadeeswaran-0788 Thank you for posting your query on Microsoft Q&A and for using Azure services.
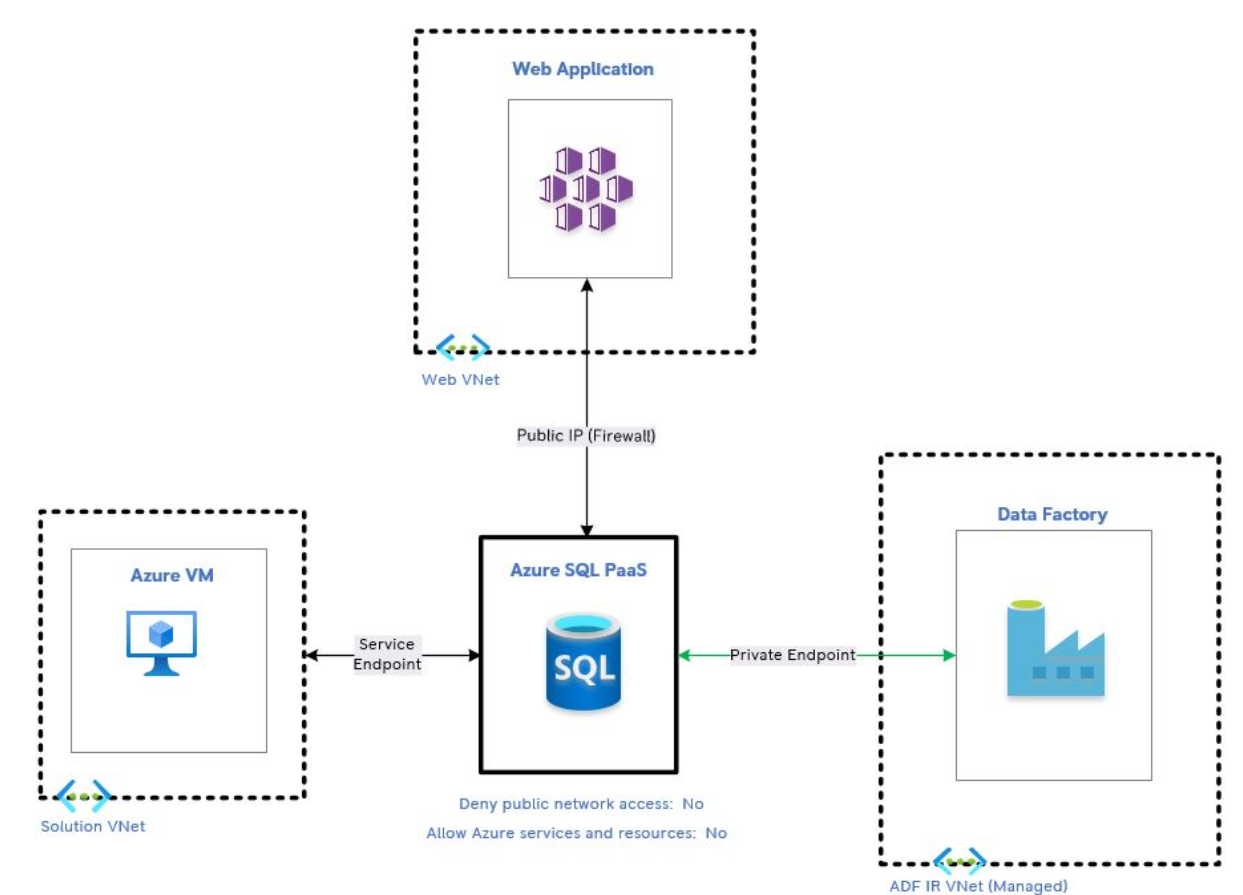
In response to this question: *I have now tested by creating a private endpoint to the VM subnet and the connectivity works from the VM to SQL. However, a VM in another subnet under the same VNet is not able to reach SQL DB. Subnets do have NSGs enforced. Not sure if this was due to DNS issue, routing or NSG rules. *
Looks like you are pinging from one subnet to another. The traffic must be able to get out of the first subnet and into the second. Therefore, you need to define both inbound and outbound rules.
See: https://learn.microsoft.com/en-us/azure/virtual-network/security-overview#default-security-rules
https://stackoverflow.com/questions/62601960/azure-vms-on-the-same-vnet-different-subnet-can-not-ping-to-port-other-then-338
Regards,
Oury