
I believe that you might have better luck by putting a user policy in place, instead of a device policy, specifically by setting the o365 password expiration policy. This will then cross devices and cover non-managed mobile and OWA access.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Hey guys,
This should be a pretty straight forward question - but I'm honestly scratching my head with this simple task and even have a ticket open with Microsoft and we still can't get this to work.
My end goal is force users to be compliant. I currently have a device configuration policy which asks users to change their password every 2 months. They get this prompt and ignore it. I have a compliance policy which catches this, marks their device as non-compliant, sends the user a push notification, and emails the user. They still ignore the request. Under the compliance rules, I can retire the device, but that seems a little overkill. Besides, it makes more work for me that I'll probably have to re-enroll the user.
So I'm trying to use a conditional access policy to block the Outlook mobile app from working on their device. It would be great if I could block all Microsoft apps that we push to the user from Company Portal (Teams, Office, OneDrive, etc.)
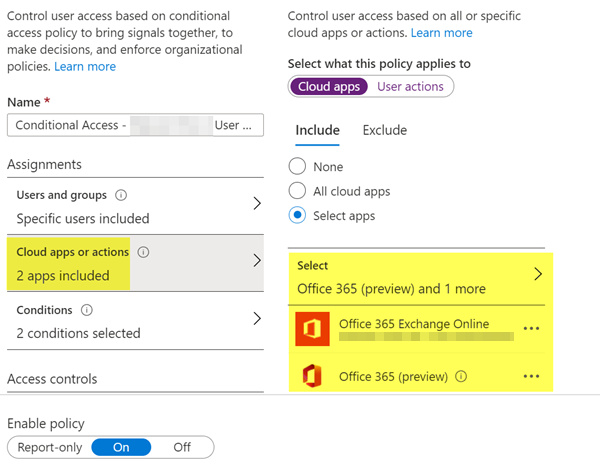
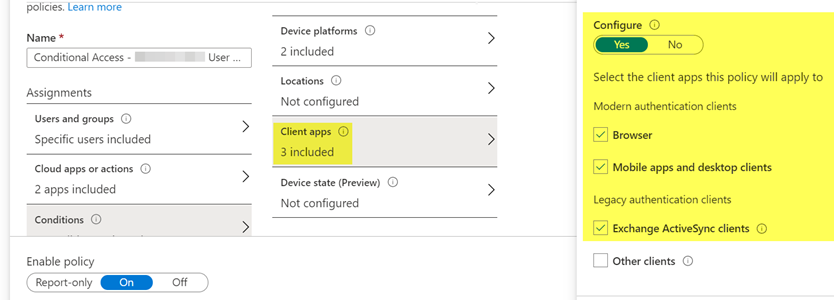
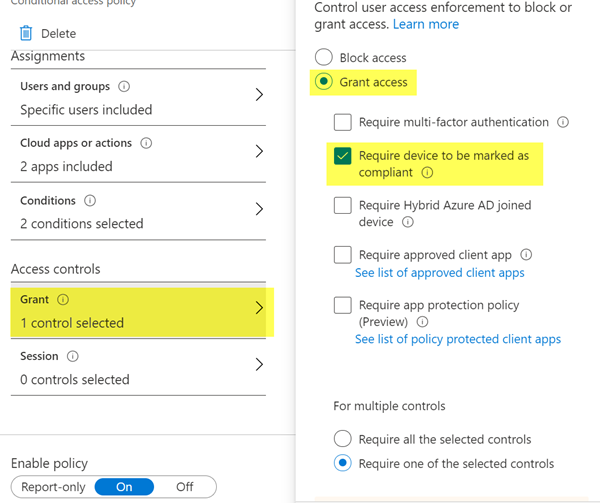
I am testing a conditional access policy with my test user on my test phone. The policy is explicitly assigned to only my test user. Under Assignments / Cloud apps or actions I have selected Office 365 Exchange Online and Office 365 (preview). Under conditions I have selected iOS and Android for the platforms, and under Client apps I have checked off Browser and Mobile apps and desktop clients under Modern authentication clients, and checked off Exchange Active Sync clients under Legacy authentication clients. Finally, under Access controls, under Grant, I have Grant access selected and checked off Require device to be marked as compliant.
The policy is enabled. I have purposely made my test device with my test user non-compliant. Endpoint manager and the device itself both report that the phone is non-compliant. But for the life of me, I cannot restrict access to the mobile apps on the phone itself.
I'm obviously missing something. And it's probably something very simple and obvious, but I'm hoping someone reading this can help me out. I've checked out the Microsoft documentation online and even the MS rep I'm dealing with is telling me everything looks good.
Other notes - my test user does have a 365 E3 license. Outlook works fine on the phone. My environment is setup as Hybrid as we're still in the process of migrating users to 365.
Thanks in advance.
Here are some screen captures.
Cloud Apps selected
Client App Condition selected
Grant Access with the one requirement selected

I believe that you might have better luck by putting a user policy in place, instead of a device policy, specifically by setting the o365 password expiration policy. This will then cross devices and cover non-managed mobile and OWA access.

What do the Sign In Logs show?
They should show what policies were applied and if not successful, what criteria was not satisfied or not configured. That should help you determine where the gap is.
BTW - for any new policy, you don't need to configure the Conditions for Client Apps:
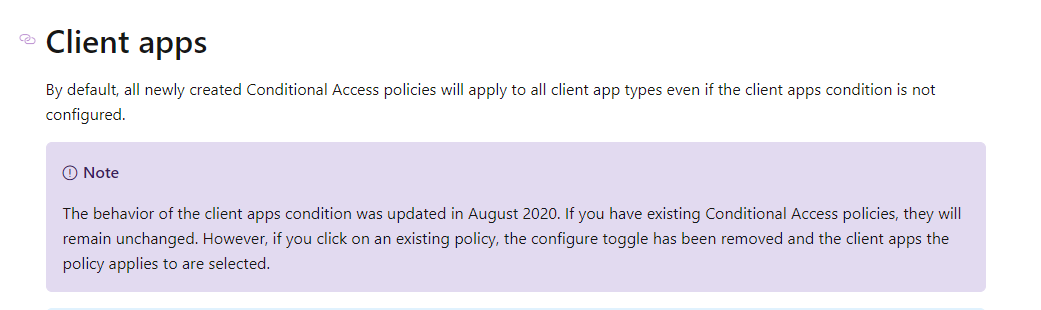
Also some articles for troubleshooting:
https://learn.microsoft.com/en-us/mem/intune/protect/troubleshoot-conditional-access#noncompliant-device-is-not-blocked
It looks like that the CA policy is not applying. Did you verify it in the sign-in logs? Also, since the policy is meant for managed devices, it maybe worth while to also add the grant control for required approved apps and enable the option require all selected controls.