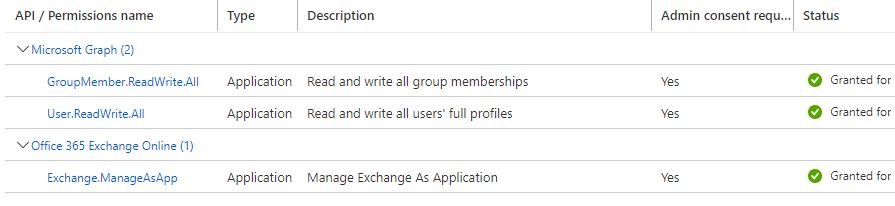
Tested assignment of Global Administrator Role to the RunAsAccount via
Add-AzureADDirectoryRoleMember -ObjectId (Get-AzureADDirectoryRole | where-object {$_.DisplayName -eq "Global Administrator"}).Objectid -RefObjectId $servicePrincipalObjectId
and it permits the RunBook to make changes to the Azure user and Azure group.
This is unacceptable as a solution because of granting too much permission.