I solve the problem by change the field from Microsoft.Network/virtualNetworks/subnets/networkSecurityGroup.id to Microsoft.Network/virtualNetworks/subnets[*].networkSecurityGroup.id
this can work when create a virtual machine
Azure policy to restrict virtual machine must add securitygroup
according to https://learn.microsoft.com/en-us/azure/templates/microsoft.compute/virtualmachines?tabs=bicep
the template shows the [networkSecurityGroup] under [networkProfile], and many other properties
but actually in a VM's Resource JSON it only has the attr [networkInterfaces] "even if securitygroup is added", I need to make this limit by attr [networkSecurityGroup], is it possible?
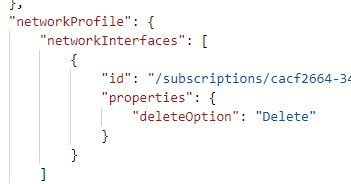
this is my azure policy, it can work but it will always deny because it can't find networkSecurityGroup
"policyRule": {
"if": {
"allOf": [
{
"field": "type",
"equals": "Microsoft.Compute/virtualMachines"
},
{
"field": "Microsoft.Compute/virtualMachines/networkProfile.networkInterfaceConfigurations[*].networkSecurityGroup.id",
"exists": false
}
]
},
"then": {
"effect": "deny"
}
}
1 answer
Sort by: Most helpful
-
Chen jun Gao (BeyondSoft consulting) 21 Reputation points
2022-05-20T07:15:28.51+00:00
