Hello @Tortigar ,
Thanks for reaching out and apologies for the delayed response.
This occurs when the Azure AD Application Proxy connector can establish a TCP connection to the backend server's IP address (based on the hostname in the internal URL - for example, https://app1.contoso.com/ - hostname stated in bold), but it is unable to negotiate an SSL session.
These are the most common root causes of this problem.
- Network problem - Incorrect TLS protocol setup (protocol, cipher suite, algorithm, there are further settings)
- No certificate or an invalid certificate is bound on the backend server
- The connector server is unable to validate the server's SSL certificate (name mismatch, expired certificate etc.)
In this scenario, the "Azure AD Application Proxy Connector Event Logs" provide more info regarding Bad Gateway difficulties (such as Secure Sockets Layer (SSL)) failures, and example Admin logs are provided below for your reference.
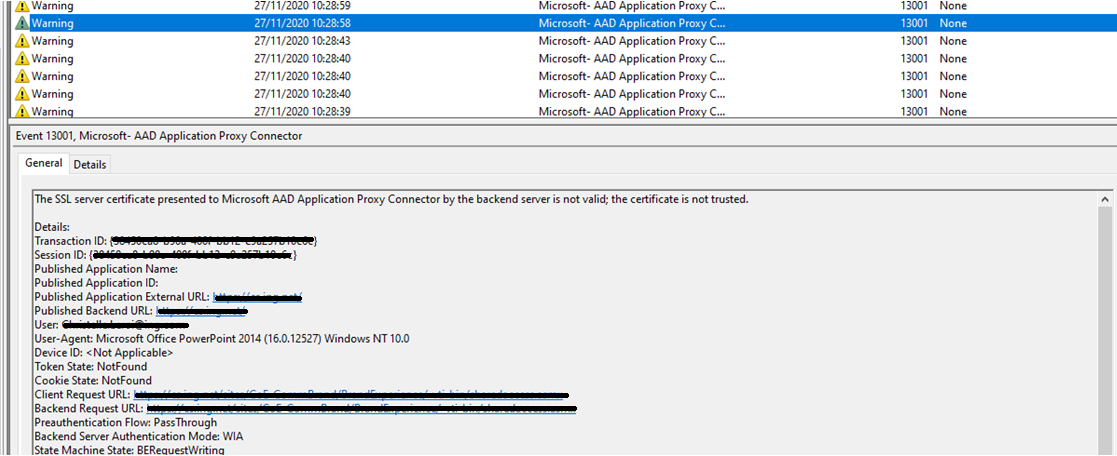
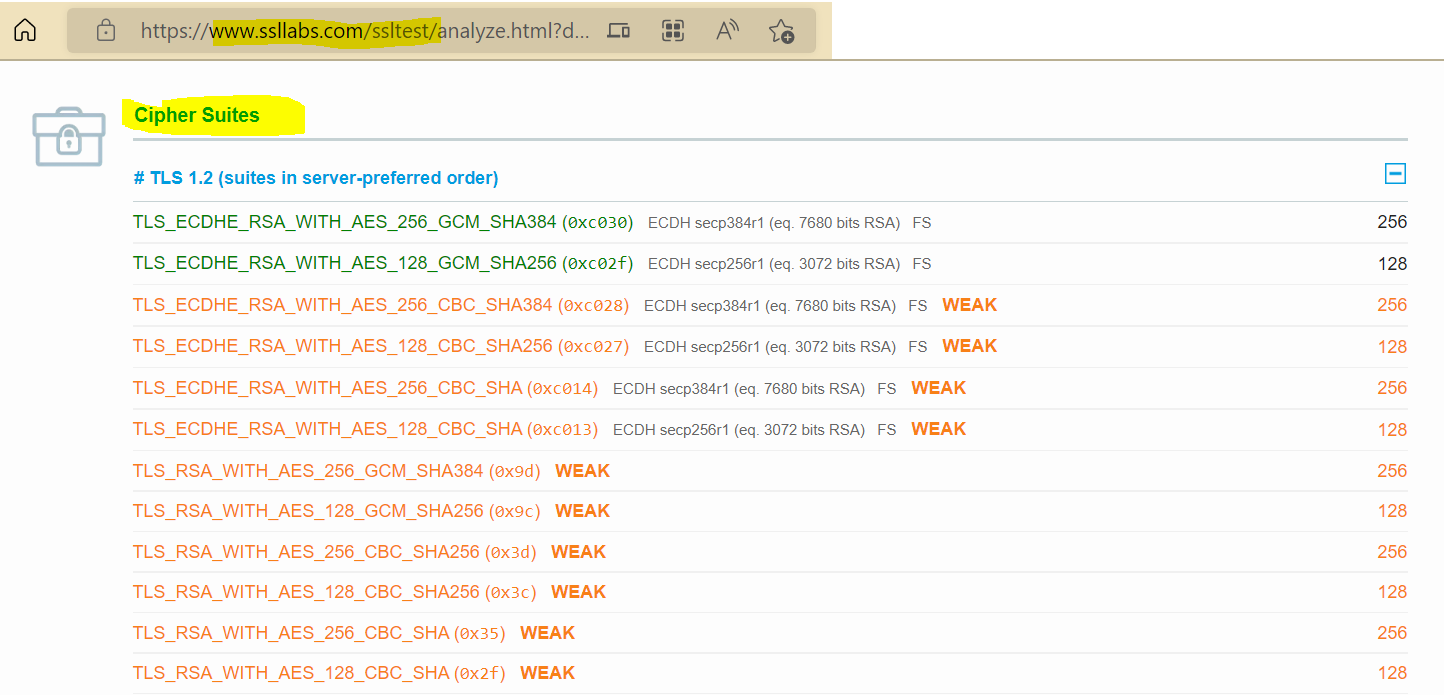
To answer your question related with cipher suite, you can use following site https://www.ssllabs.com/ssltest/analyze.html? to validate list of suites in server-preferred order and make sure you have them configured in your NGINX server and below is for your reference.
If none of these work, I would recommend you to reach out to Azure support because this would require a more extensive investigation. If you do not have a support plan, please send an email with the subject line “Attn: SivaKumarS” to AzCommunity[at]Microsoft[dot]com referencing this article and your subscription id, and we will help you get one-time free technical support.
Hope it helps!!!
-----
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.
