The easiest way to run the non-compliances key vault query is to use the Microsoft Defender for cloud blade. Navigate to
Home > Microsoft Defender for Cloud > Security Posture > View Recommendations > Expand the Key Vault then open in Resource Explorer
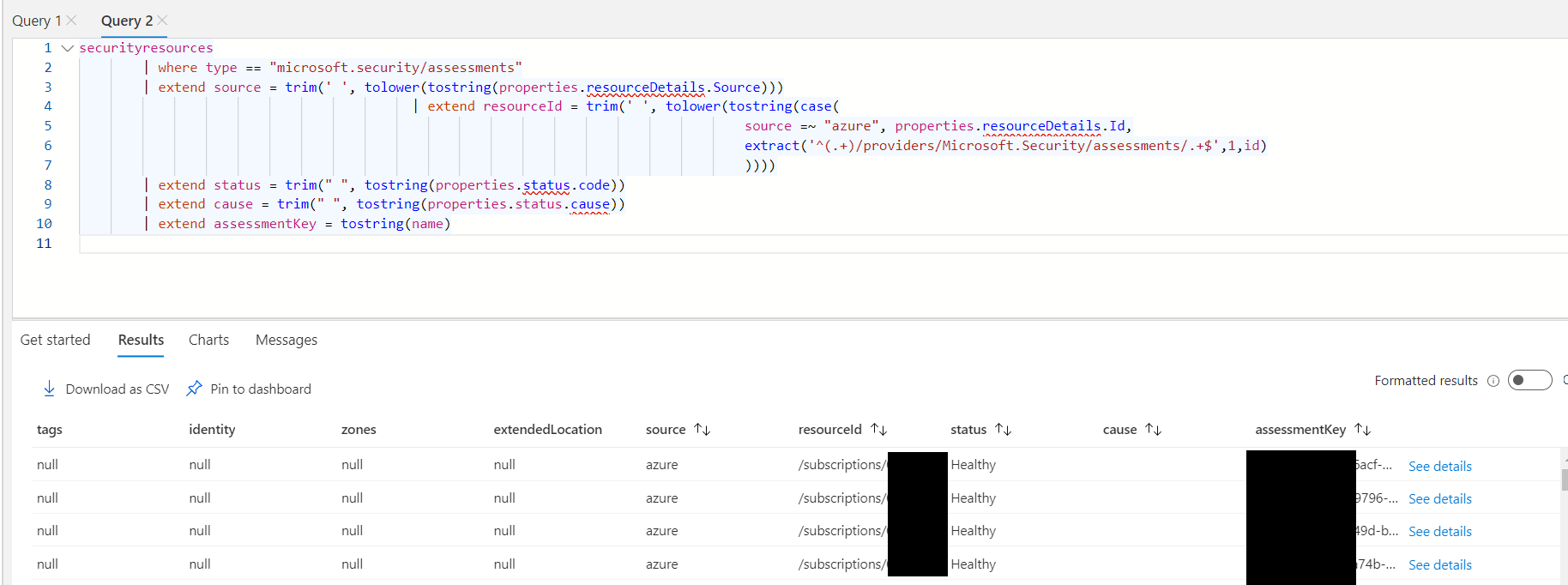
Or you can use the query like this (copied from the same section), you can include an additional where clause
securityresources
| where type == "microsoft.security/assessments"
| extend source = trim(' ', tolower(tostring(properties.resourceDetails.Source)))
| extend resourceId = trim(' ', tolower(tostring(case(
source =~ "azure", properties.resourceDetails.Id,
extract('^(.+)/providers/Microsoft.Security/assessments/.+$',1,id)
))))
| extend status = trim(" ", tostring(properties.status.code))
| extend cause = trim(" ", tostring(properties.status.cause))
| extend assessmentKey = tostring(name)