You’re likely correct.
By switching to ‘just’ https, you’re saying that all requests must use https and not http.
This means your cert must be configured correctly.
A trusted/signed certificate is needed.
Here’s a walkthrough demo that might help.
how-to-configure-pki-for-microsoft-sccm-to-use-https-ssl-instead-of-http
Switching to PKI Issue
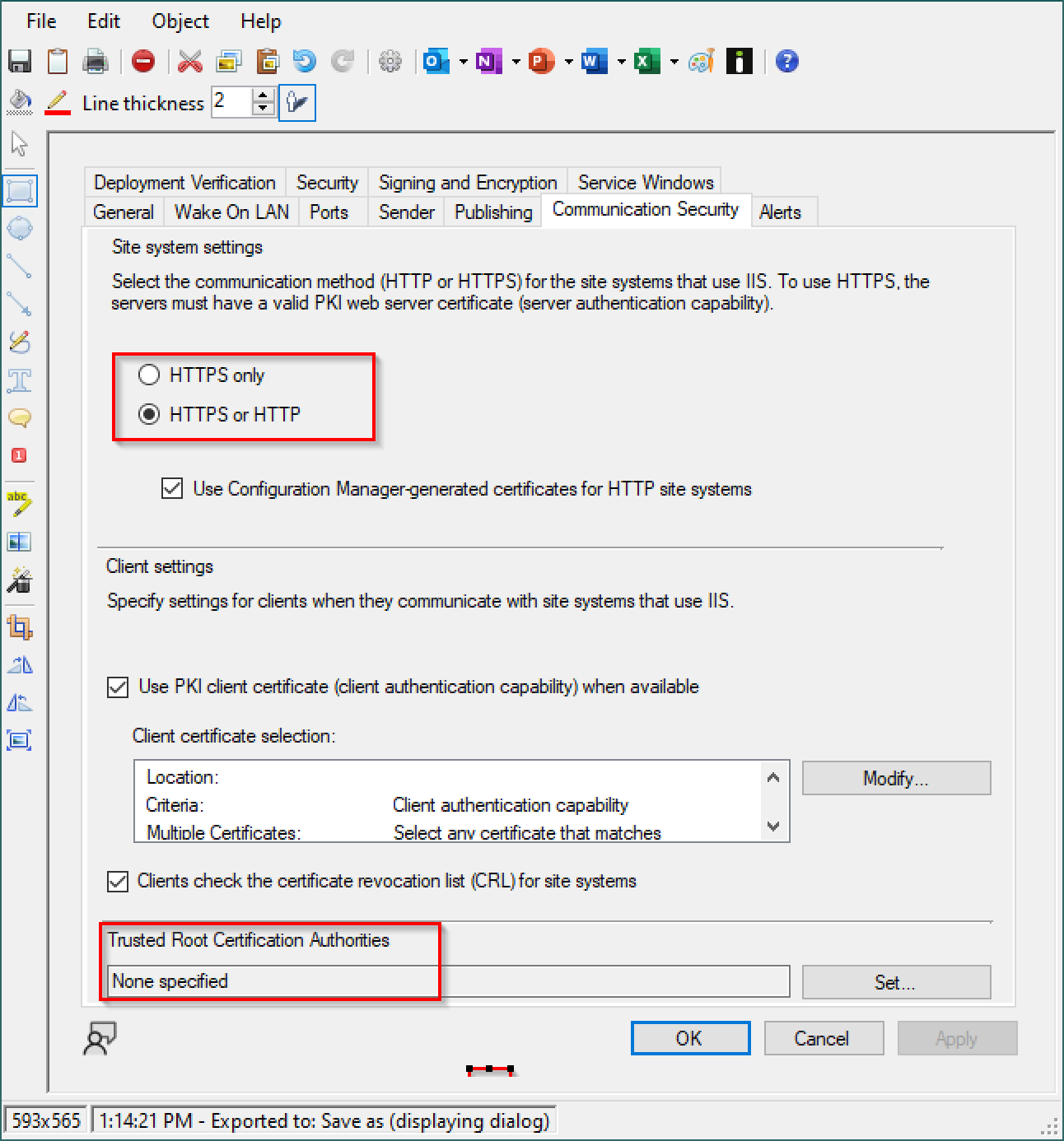
We recently started the process of switching to PKI (followed the MVP days document) , everything works well, clients got the cert, WSUS is using SSL as well as IIS. Client stop communicating when we try to change the following to HTTPS. I was thinking it was because I did not specify a ROOT CA, however I did not specify one in the lab I built either.
any help greatly appreciated.
Microsoft Security | Intune | Configuration Manager | Other
4 answers
Sort by: Most helpful
-
 David Broggy 6,371 Reputation points MVP Volunteer Moderator
David Broggy 6,371 Reputation points MVP Volunteer Moderator2022-05-26T03:11:56.34+00:00 -
Belgian Malinois 461 Reputation points
2022-05-27T12:44:11.51+00:00 @David Broggy I actually watched that vide and he has the same settings as I do, so I wonder if it can remain this way.
If not, scan that be the same cert as the clients have on their machines? -
Belgian Malinois 461 Reputation points
2022-05-27T22:50:28.343+00:00 Adding the Client certificate as the ROOT CA did the trick
-
 AllenLiu-MSFT 49,316 Reputation points Microsoft External Staff
AllenLiu-MSFT 49,316 Reputation points Microsoft External Staff2022-05-30T07:47:40.627+00:00 Thank you for posting in Microsoft Q&A forum.
Glad to hear that you fixed the issue, here is the information from the documentation:
When you issue client PKI certificates from the same CA hierarchy that issues the server certificates that you use for management points, you don't have to specify this root CA certificate. However, if you use multiple CA hierarchies and you aren't sure whether they trust each other, import the root CA for the clients' CA hierarchy.
If the answer is the right solution, please click "Accept Answer" and kindly upvote it. If you have extra questions about this answer, please click "Comment".
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.