Hello,
For a start you should check the information below in your environment:
Check whether this machine has configured certificate auto enrollment GPO.
Check whether the certificate template is issued on CA server.
Check whether the machine has read, enroll and autoenroll permissions for this certificate template.
Check whether all machines or only one machine has such issue.
If it does not work above, because certificate templates are stored on DCs not CA server, please check AD replication is working fine by running repadmin /showrepl and repadmin /replsum.
For various reasons, the GPO you have created may not actually be applying to the workstation. To verify this, you can use the Registry Editor.
Press the Windows+R keys in combination on your keyboard to bring up the Run prompt. Type regedit and press OK.
In the tree-view on the left, navigate to HKLM\Software\Policies\Microsoft\Cryptography\AutoEnrollment and verify the value of AEPolicy is set to 0x00000007.
In the tree-view on the left, navigate to HKCU\Software\Policies\Microsoft\Cryptography\AutoEnrollment and verify the value of AEPolicy is set to 0x00000007.
If either of these values are incorrect, the GPO you created is not applying correctly. You will want to use standard GPO troubleshooting tools such as gpupdate /force and gpresult /h to troubleshoot this further.
Note: for more information about these registry values, you can read a Microsoft blog post about them here.
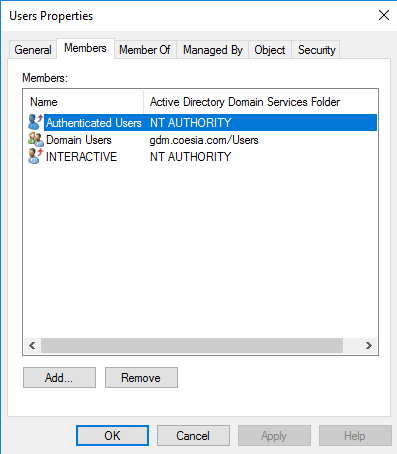
Certificate Template Permissions
If the user, or a group the user is a member of, does not have the correct permissions on the certificate template the prompt will not appear. On the certificate template, verify that the permissions for your user (or group) on the security tab of the template properties are as below.
Read: Allow
Enroll: Allow
Autoenroll: Allow
User Already Has a Certificate in the Certificate Store
If the user already has a certificate in the Personal certificate store, it will assume auto-enrollment has already taken place and will not prompt. To verify this, you can use the certificates MMC.
Press the Windows+R keys in combination on your keyboard to bring up the Run prompt. Type mmc and press OK.
Note: If prompted by UAC to run MMC as administrator, select Yes.
Click File > Add/Remove Snap-in...
Select Certificates from the Available Snap-ins, press Add >.
Ensure My user account is selected and press Finish.
Press OK.
In the tree view on the left hand, navigate to Certificates - Current User\Personal\Certificates.
In the main view, check to see if there are any certificates issued to your user. If so, delete them and then next time you log in, the auto-enrollment prompt should appear.
Additional Steps
If the auto-enrollment prompt/tray icon still do not appear, consider the following additional steps.
Use certutil -pulse to pulse auto-enrollment events.
Force a Group Policy update by running gpupdate /force.
Have the user reboot and log back in.
Wait up to 8 hours to make sure smart card-related configuration has propagated within the domain.
The command certreq -enroll <TEMPLATENAME>, where <TEMPLATENAME> is the name of your certificate template can be used instead of the tray icon to kick off the Certificate Enrollment wizard.
--If the reply is helpful, please Upvote and Accept as answer--
 ]
]