@VaishnavAV-2087 My suggestion will be to use the Locks inheritance and apply lock at resource group level.
Regards,
Oury
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
I am trying to define a policy that will deploy a delete lock at the resource level for Azure MYSQL DB without locks. Below is my code please help me modify the code to set delete lock at the resource level instead of the resource group.
"policyRule": {
"if": {
"allOf": [
{
"field": "type",
"equals": "Microsoft.DBforMySQL/servers"
}
]
},
"then": {
"effect": "deployIfNotExists",
"details": {
"type": "Microsoft.Authorization/locks",
"existenceCondition": {
"field": "Microsoft.Authorization/locks/level",
"equals": "CanNotDelete"
},
"roleDefinitionIds": [
"/providers/Microsoft.Authorization/roleDefinitions/8e3af657-a8ff-443c-a75c-2fe8c4bcb635"
],
"deployment": {
"properties": {
"mode": "incremental",
"template": {
"$schema": "https://schema.management.azure.com/schemas/2015-01-01/deploymentTemplate.json",
"contentVersion": "1.0.0.0",
"resources": [
{
"type": "Microsoft.Authorization/locks",
"apiVersion": "2017-04-01",
"name": "DeleteLock",
"properties": {
"level": "CanNotDelete",
"notes": "Prevent deletion of the resource group"
}
}
]
}
}
}
}
}
}

@VaishnavAV-2087 My suggestion will be to use the Locks inheritance and apply lock at resource group level.
Regards,
Oury

In addition to the above answer, I suggested regarding using locks inheritance and apply lock at the resource level group.
You can create a one-time custom Azure Policy with below definition and ensure that a remediation task is set.
Any Azure MySQL resource created in the policy assignment scope is evaluated, and a resource lock is created for it, if it does not exist.
With below policy, resource lock will be limited to Azure MySQL scope, not resource group scope, just as customer required.
And it does not require you to specify a particular server name either – this policy will pick up the server's name from the target resource against which policy is being evaluated.
{
"properties": {
"displayName": "Deploy CanNotDelete Resource Lock on MySQL resources",
"description": "Creates a resource lock for a MySQL resource.",
"mode": "all",
"metadata": {
"version": "1.0.0",
"category": "General"
},
"parameters": {},
"policyRule": {
"if": {
"field": "type",
"equals": "Microsoft.DBforMySQL/flexibleServers"
},
"then": {
"effect": "DeployIfNotExists",
"details": {
"type": "Microsoft.Authorization/locks",
"existenceCondition": {
"field": "Microsoft.Authorization/locks/level",
"equals": "CanNotDelete"
},
"roleDefinitionIds": [
"/providers/Microsoft.Authorization/roleDefinitions/8e3af657-a8ff-443c-a75c-2fe8c4bcb635"
],
"deployment": {
"properties": {
"mode": "incremental",
"template": {
"$schema": https://schema.management.azure.com/schemas/2015-01-01/deploymentTemplate.json,
"contentVersion": "1.0.0.0",
"parameters": {
"serverName": {
"type": "string"
}
},
"resources": [
{
"type": "Microsoft.Authorization/locks",
"apiVersion": "2017-04-01",
"scope": "[concat('Microsoft.DBforMySQL/flexibleServers/', parameters('serverName'))]",
"name": "DenyDelete",
"properties": {
"level": "CanNotDelete",
"notes": "Prevents deletion of resource."
}
}
]
},
"parameters": {
"serverName": {
"value": "[field('name')]"
}
}
}
}
}
}
}
}
}
Same as the image posted below
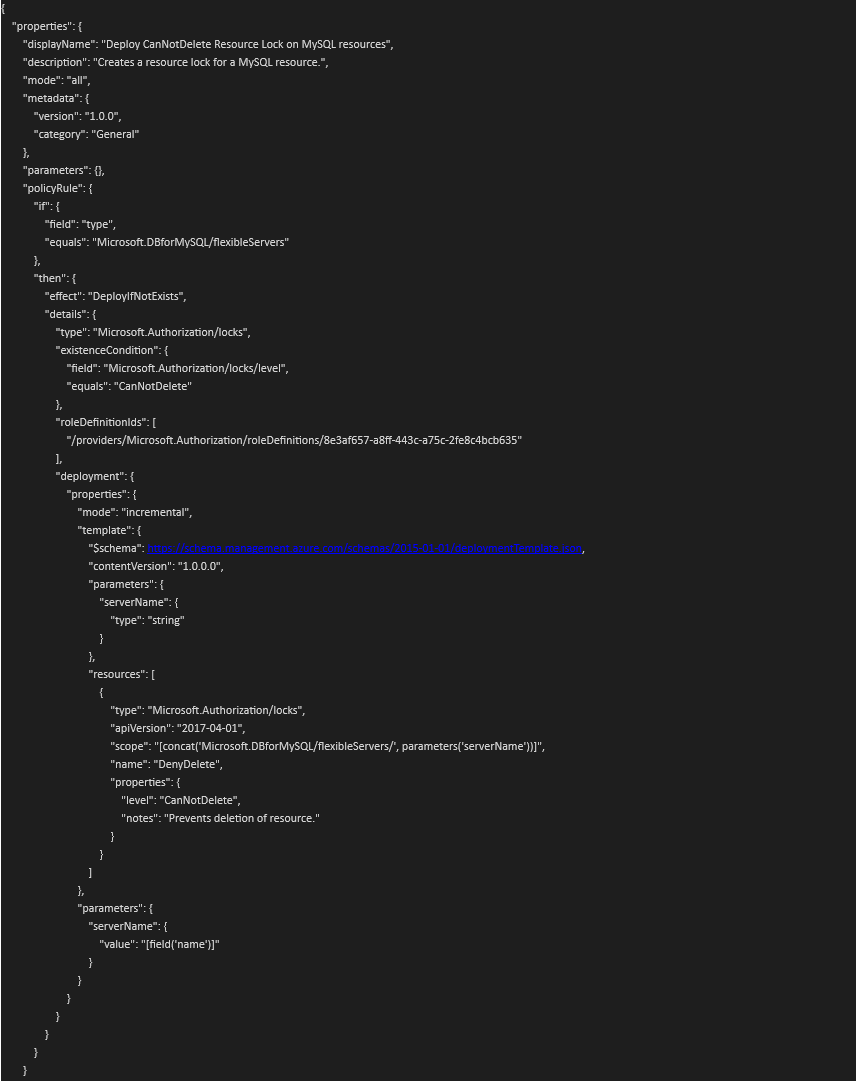
Please let us know if you have any questions. Feel free to comment below so we can discuss further
Regards,
Oury

@VaishnavAV-2087 Thank you for posting your question on Microsoft Q&A and for using Azure services.
My understanding is that you are trying to modify the above code to deploy a delete lock for your Azure MYSQL at the resource level instead of the resource group level.
Please let me know if my understanding is not correct.
This ARM template deploys Azure Database for MySQL Server and creates a CanNotDelete Lock to avoid accidental deletion of the server.
NOTE: To create or delete management locks, you must have access to Microsoft.Authorization/* or Microsoft.Authorization/locks/* actions. Of the built-in roles, only Owner and User Access Administrator are granted those actions.
Could you please the below code and let me know if that works for you.
"if": {
"field": "type",
"equals": "Microsoft.DBforMySQL/servers"
},
"then": {
"effect": "deployIfNotExists",
"details": {
"type": "Microsoft.Authorization/locks",
"existenceCondition": {
"field": "Microsoft.Authorization/locks/level",
"equals": "CanNotDelete"
},
"roleDefinitionIds": [
"/providers/Microsoft.Authorization/roleDefinitions/8e3af657-a8ff-443c-a75c-2fe8c4bcb635"
],
"deployment": {
"properties": {
"mode": "incremental",
"template": {
"$schema": "https://schema.management.azure.com/schemas/2015-01-01/deploymentTemplate.json",
"contentVersion": "1.0.0.0",
"resources": [
{
"type": "Microsoft.DBforMySQL/servers/providers/locks",
"apiVersion": "2016-09-01",
"name": "[concat(parameters('serverName'), '/Microsoft.Authorization/serverLock')]",
"dependsOn": [
"[resourceId('Microsoft.DBforMySQL/servers', parameters('serverName'))]"
],
"properties": {
"level": "CanNotDelete",
"notes": "[concat('MySQL Server ', parameters('serverName'), ' should not be deleted.')]"
}
}
]
Source:
Understand Azure Policy effects
https://github.com/Azure/azure-mysql/blob/master/arm-templates/ExampleWithLocks/template.json
Regards,
Oury