Thank you for reaching out to us. As I understand you have implemented “Use case 3” from article Azure AD Connect : Customize Sync Options - TechNet Articles - United States (English) - TechNet Wiki (microsoft.com).
As per article you have created 2 different custom rules in AD connect. One rule is to block all users from syncing to Azure AD and one rule is to sync only few users with specific value mentioned in specific attribute.
I configured the same in my lab and it works as expected. To take this further we will have to check the rule with higher priority.
You can export the rule by selecting the rule and clicking on export.
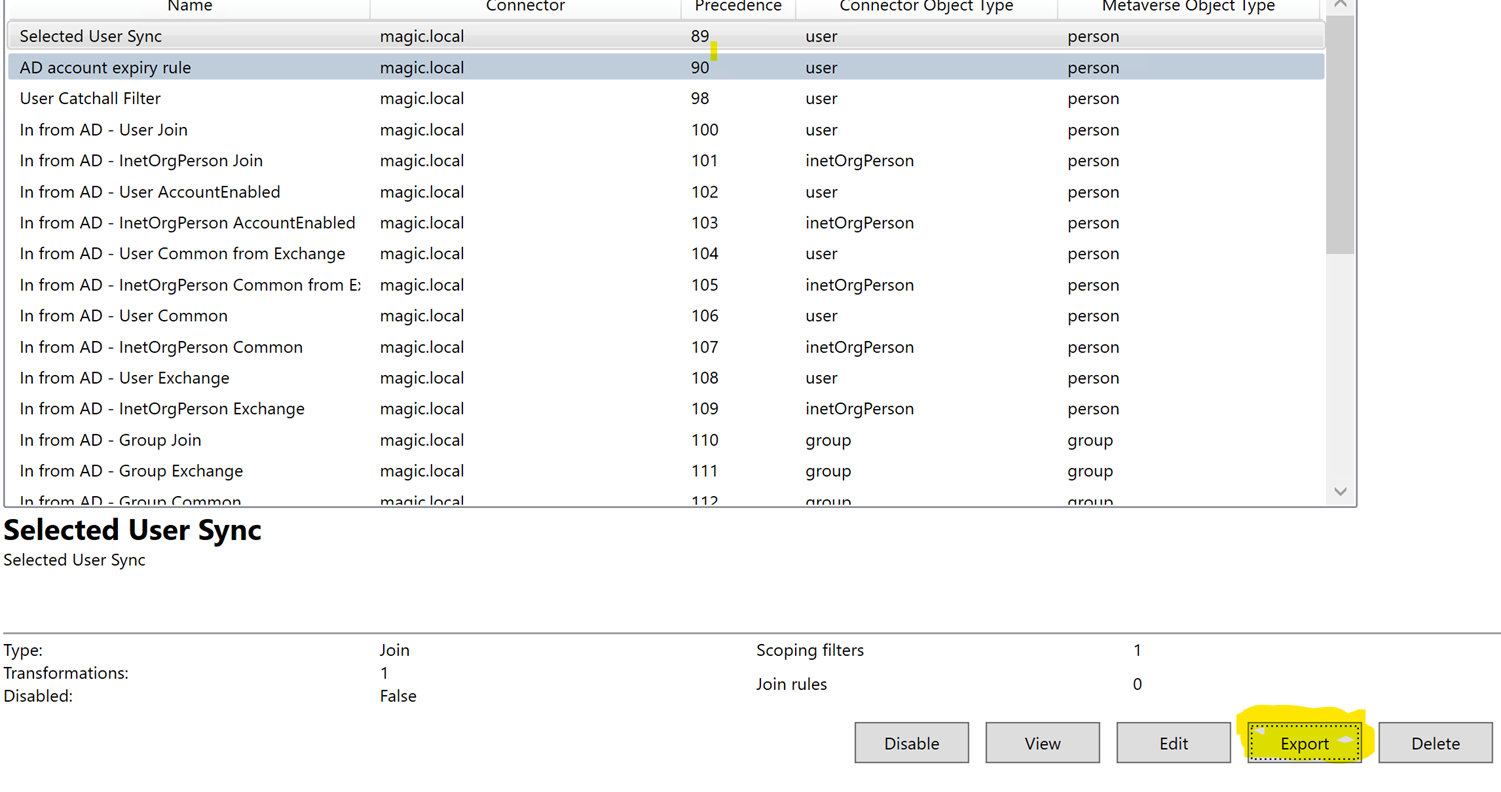
The rule should look something like below,
New-ADSyncRule \-Name 'Selected User Sync'
-Identifier 'e80fa9f6-5931-43ed-9b4d-b814180dfe26' \-Description 'Selected User Sync'
-Direction 'Inbound' \-Precedence 89
-PrecedenceAfter '00000000-0000-0000-0000-000000000000' \-PrecedenceBefore '00000000-0000-0000-0000-000000000000'
-SourceObjectType 'user' \-TargetObjectType 'person'
-Connector 'e4212bf2-c549-4145-91c9-e719a705019e' \-LinkType 'Join'
-SoftDeleteExpiryInterval 0 \-ImmutableTag $null
-OutVariable syncRule
Add-ADSyncAttributeFlowMapping \-SynchronizationRule $syncRule[0]
-Source @('False') \-Destination 'cloudFiltered'
-FlowType 'Constant' \-ValueMergeType 'Update'
-OutVariable syncRule
New-Object \-TypeName 'Microsoft.IdentityManagement.PowerShell.ObjectModel.ScopeCondition'
-ArgumentList 'extensionAttribute1','sync','EQUAL' `
-OutVariable condition0
Add-ADSyncScopeConditionGroup \-SynchronizationRule $syncRule[0]
-ScopeConditions @($condition0[0]) `
-OutVariable syncRule
Add-ADSyncRule `
-SynchronizationRule $syncRule[0]
Get-ADSyncRule `
-Identifier 'e80fa9f6-5931-43ed-9b4d-b814180dfe26'
You can compare the rule and let me confirm if it is configured correctly.
