This is the correct scope to use for the client credentials flow you can check the scopes the token receives in jwt.io, if you don't see the Mail.Read/Mail.ReadWrite in the Access token it's most likely they have granted the Delegate permission rather then the Application permissions for those permission there is a Delegate and Application permission. Ask the admin to send a screen shot of the permissions if you see delegate next to name of the permission then you know that's the issue.
Fail to get access token on https://graph.microsoft.com/mail.read/.default
I am trying to build an application to access emails of Office 365 using Microsoft OAuth authentication and Microsoft Graph API.
An application has been registered at Corporate tenant, and granted permission on Microsoft Graph Mail.Read/Mail.ReadWrite by tenant admin, and I have the necessary information (tenant ID, client Id -- application Id, client secret).
When I try to get access token, it gives me some error:
{"error":"invalid_resource",
"error_description":"AADSTS500011: The resource principal named https://graph.microsoft.com/Mail.ReadWrite was not found in the tenant named Corporate. This can happen if the application has not been installed by the administrator of the tenant or consented to by any user in the tenant. You might have sent your authentication request to the wrong tenant.\r\nTrace ID: 63eff76d-dbc5-4e98-984e-235c73cbf700\r\nCorrelation ID: bae48b83-cb1f-4288-82b5-233216e9fb55\r\nTimestamp: 2022-06-01 15:30:13Z",
"error_codes":[500011],
"timestamp":"2022-06-01 15:30:13Z",
"trace_id":"63eff76d-dbc5-4e98-984e-235c73cbf700",
"correlation_id":"bae48b83-cb1f-4288-82b5-233216e9fb55",
"error_uri":"https://login.microsoftonline.com/error?code=500011"}
I use .net ConfidentialClientApplicationBuild.AcquireTokenForClient, to get the access token.
The scope used: https://graph.microsoft.com/Mail.Read/.default
When I used scope https://graph.microsoft.com/.default, I could get token.
What do I need to do to get access on https://graph.microsoft.com/Mail.Read ?
Microsoft Security Microsoft Authenticator
Microsoft Security Microsoft Graph
1 additional answer
Sort by: Most helpful
-
 CarlZhao-MSFT 46,371 Reputation points
CarlZhao-MSFT 46,371 Reputation points2022-06-03T08:24:29.543+00:00 Hi @Sun, Yajun
This is an expected error, the client credential flow uses static permissions by default, so it only supports the
/.defaultscope. However, this means that the token you get will contain all the granted application permissions, which is obviously too much for your token from a least privilege point of view.If you just want to grant your application specific permissions dynamically I recommend you to use the auth code flow. The benefit of this authentication flow is that you don't need to pre-grant permissions in the Azure portal at all, you can specify the scopes your application needs at any time by including the new scopes in the scope parameter when requesting an access token - without the need to pre-define them in the application registration information.
using Microsoft.Identity.Client; namespace test1 { class Program { static async System.Threading.Tasks.Task Main(string[] args) { string clientId = "{client id}"; string clientSecret = "{client secret}"; string redirectUri = "https://jwt.ms"; string authority = "https://login.microsoftonline.com/{tenant id}"; string authorizationCode = "{authorization code}"; string[] scopes = new string[] { "https://graph.microsoft.com/Mail.Read" }; IConfidentialClientApplication app = ConfidentialClientApplicationBuilder .Create(clientId) .WithRedirectUri(redirectUri) .WithClientSecret(clientSecret) .WithAuthority(authority) .Build(); var authResult = await app.AcquireTokenByAuthorizationCode(scopes, authorizationCode).ExecuteAsync(); Console.WriteLine(authResult.AccessToken); } }; }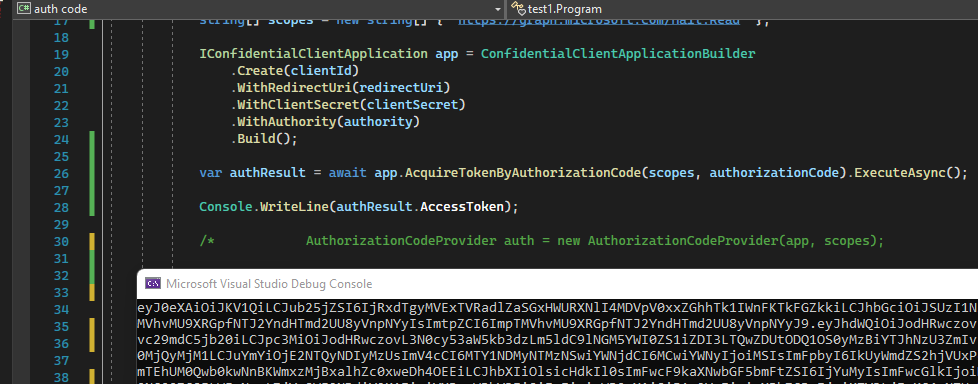
If the answer is helpful, please click "Accept Answer" and kindly upvote it. If you have extra questions about this answer, please click "Comment".
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.