Hi all,
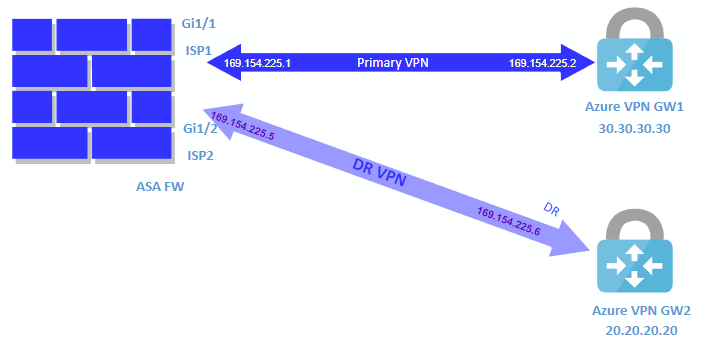
I have a Cisco ASA firewall, where if I created a Route Based VPN " gtwy, local connection and connection, I can get both a policy based and route based working on the ASA side to my Azure VPN.
My issue is, I have a ISP route with a new ISP and the peer IP is on this router. So it is doing a one to one NAT and when I do a Azure peering to this IP, where NAT-T is in use, I cannot get it to work.
Phase 1 and 2 come up on the ASA, and I see my packets being encrypted and sent through the tunnel, but I get no replies from the Azure side, even though the Connection shows Connected.
If I look at the effective routes on my test Azure VM server, I see the routes to my OnPrem subnet pointing to the Virtual gateway, and I am allowing ping through my NSG and Windows firewall, but I see no traffic hit my ASA.
Reminder, if I change this back to the IP address on my ASAs outside interface, it comes up fine and xmt and rcv works fine.
Only issue is when NAT-T is involved.
MS docs say NAT-T is supported, but I cant get it to work.