
@Tarek Halloun
Thanks for your posting on Q&A.
It is recommended to check the DefaultAUService by the following PowerShell script:
$MUSM = New-Object -ComObject "Microsoft.Update.ServiceManager"
$MUSM.Services | select Name, IsDefaultAUService
Reference screenshot in my lab:
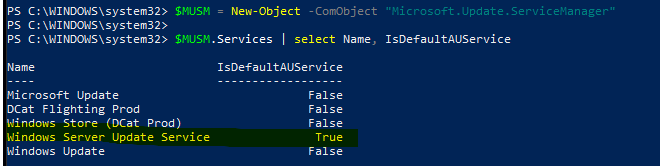
The picture indicate that the DefaultAUService is WSUS. The device will try to scan updates from WSUS first.
The following Group Policies may be helpful:
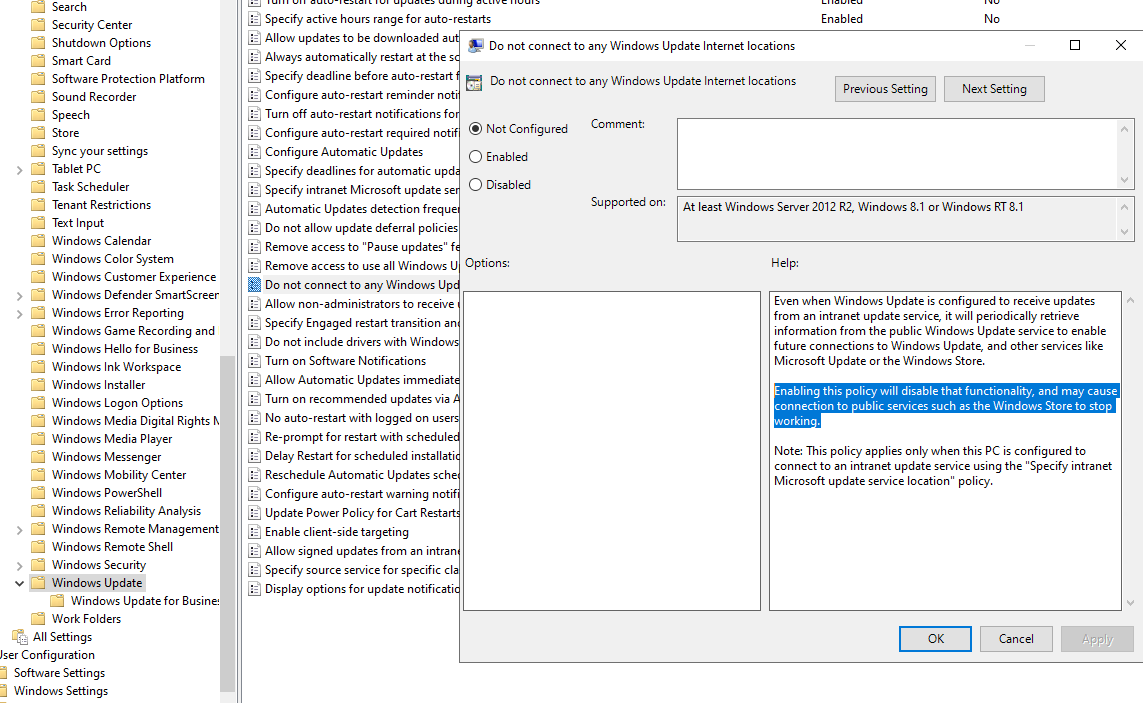
Do not connect to any Windows Update Internet locations
As we all know, we could point to devices to the WSUS Server to get updates by configure the Specify Intranet Microsoft update service location group policy. Specify Intranet Microsoft update service location allows admins to point devices to an internal Microsoft update service location(like WSUS), while Do not connect to any Windows Update Internet locations gives them the option to restrict devices to just that internal update service.
Turn off access to all Windows Update features
If you enable this policy setting, all Windows Update features are removed. This includes blocking access to the Windows Update website at http://windowsupdate.microsoft.com, from the Windows Update hyperlink on the Start menu, and also on the Tools menu in Internet Explorer. Windows automatic updating is also disabled; you will neither be notified about nor will you receive critical updates from Windows Update. This policy setting also prevents Device Manager from automatically installing driver updates from the Windows Update website.

Please learn more detail about the both group policies and we could choose one of the two according to your environment.
Hope the above will be helpful.
Best regards,
Rita
If the answer is the right solution, please click "Accept Answer" and kindly upvote it. If you have extra questions about this answer, please click "Comment".
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.