Hello @Vincent Coucharriere
Please make sure to follow the steps below (total of 8 steps)
- Enable Identity from your Azure Web App, and copy the value of the identity, you need this in step#3
- Go to the Key vault and create a secret with value
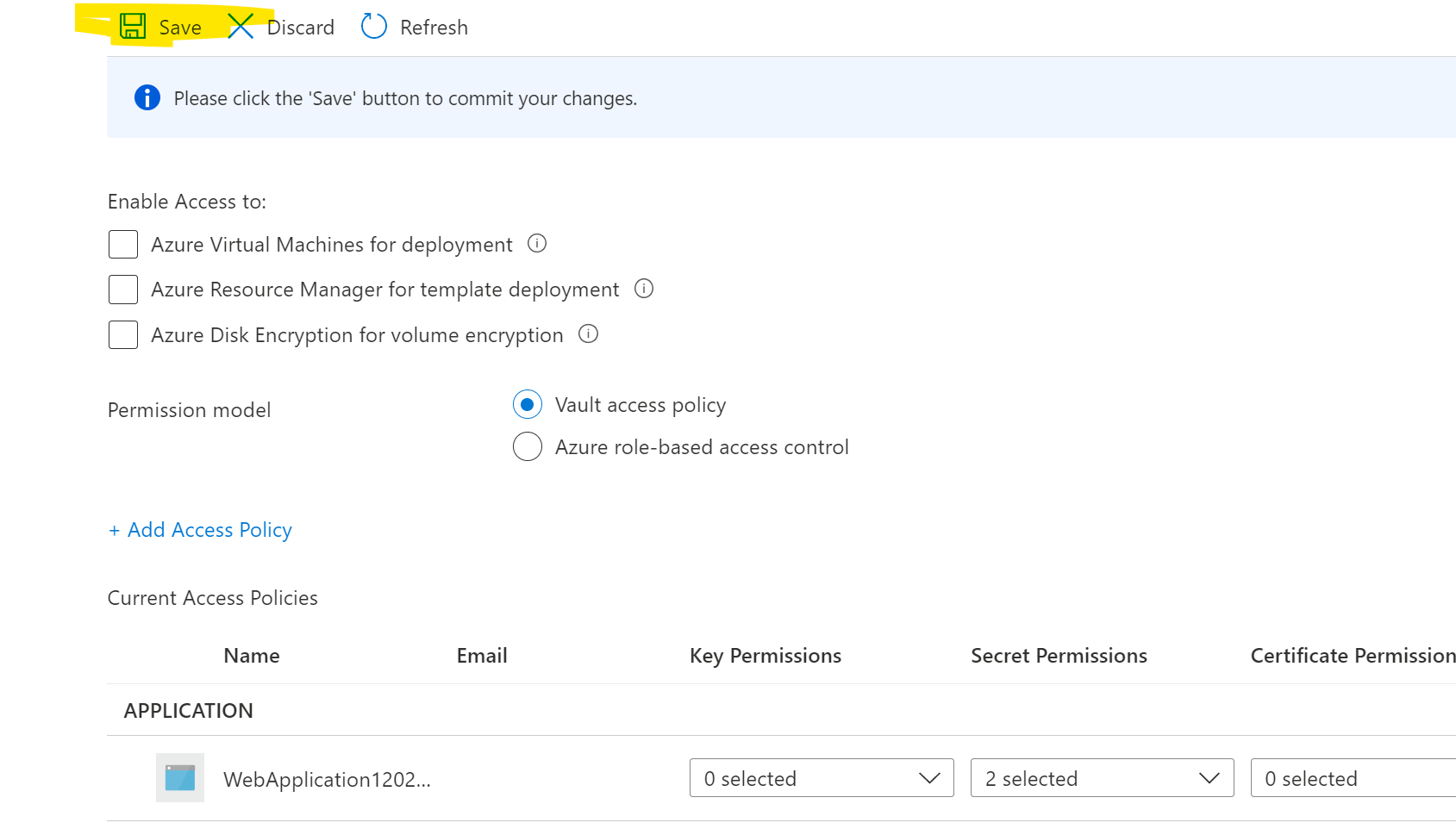
- From the key vault Click "Access Policies" Add Access Policy" then select at least "Get" from the secret permissions
- From the Select principal click "none selected" from the search box paste the GUID copied from step #1 then select and then Add
- Make sure to click "Save", lots of people miss this step
- go to your web app and add the app settings key
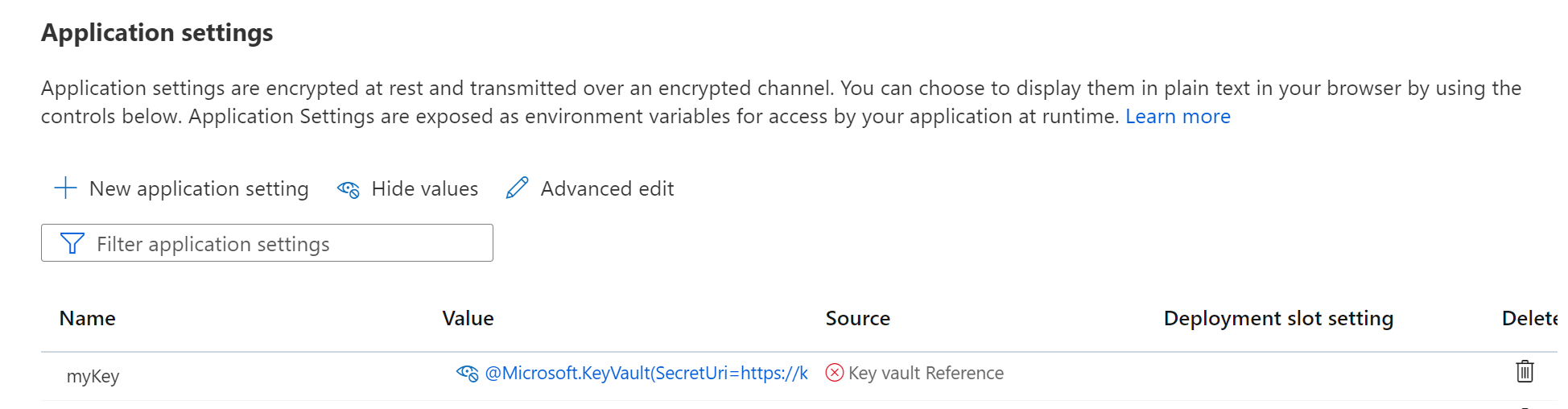
- from the step#3 if you granted "List" permission then you don't need to provide the version part it can be something like @Microsoft.KeyVault(SecretUri=https://[KVNAME].vault.azure.net/secrets/[SECRETNAME]), please note no version is here. in this case, it will always use the latest version, which is preferred if you change the value frequently

