Hi @techresearch7777777 ,
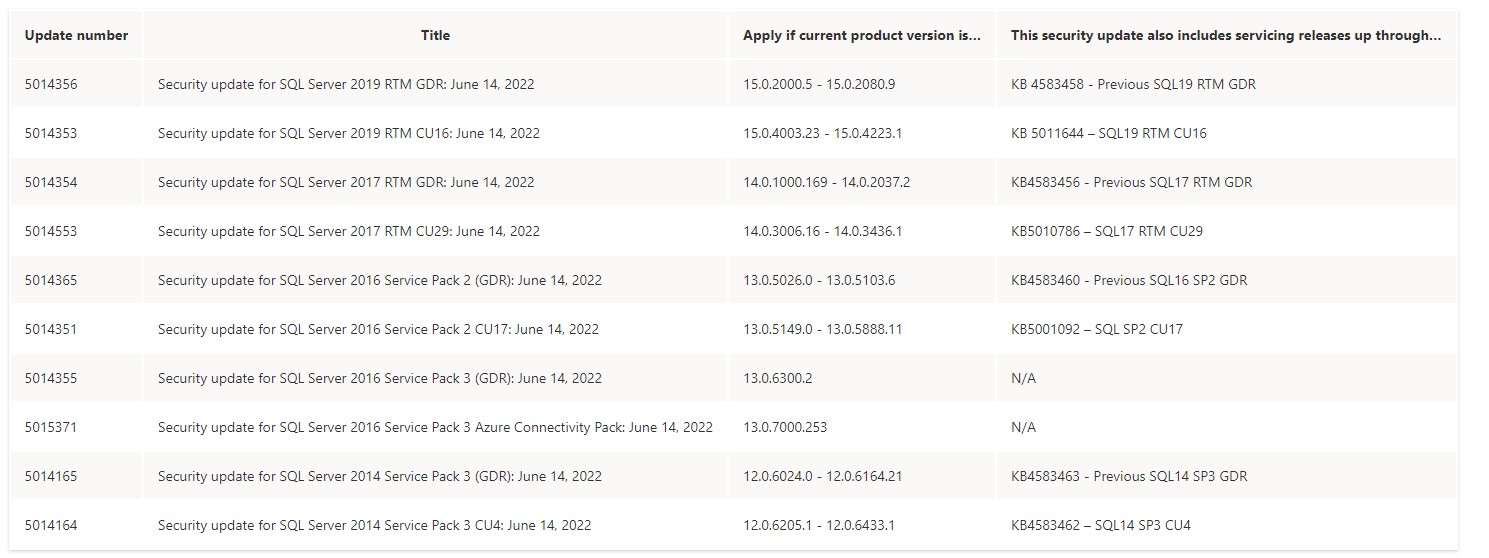
Please check the patches that you need to apply to your six SQL server instances.
Microsoft SQL Server 2014 (SP3-CU4-GDR) (KB4583462) - 12.0.6433.1 (X64) Oct 31 2020 02:54:45 Copyright (c) Microsoft Corporation Enterprise Edition: Core-based Licensing (64-bit) on Windows NT 6.3 <X64> (Build 9600: ) (Hypervisor)---------------------------Apply 5014164 Security update for SQL Server 2014 SP3 CU4: June 14, 2022 to this SQL instance.
Microsoft SQL Server 2016 (SP2-GDR) (KB4583460) - 13.0.5103.6 (X64) Nov 1 2020 00:13:28 Copyright (c) Microsoft Corporation Standard Edition (64-bit) on Windows Server 2012 R2 Standard 6.3 <X64> (Build 9600: ) (Hypervisor)---------------------------- Apply 5014365 Security update for SQL Server 2016 SP2 GDR: June 14, 2022 to this SQL server instance.
Microsoft SQL Server 2016 (SP2-GDR) (KB4583460) - 13.0.5108.50 (X64) May 20 2022 20:28:29 Copyright (c) Microsoft Corporation Standard Edition (64-bit) on Windows Server 2016 Standard 10.0 <X64> (Build 14393: ) (Hypervisor)------------------This the latest GDR for SQL server 2016 SP2. If you do not want to apply SP3 for this SQL server instance, you do not need to apply patch for this instance.
Microsoft SQL Server 2016 (SP3) (KB5003279) - 13.0.6300.2 (X64) Aug 7 2021 01:20:37 Copyright (c) Microsoft Corporation Developer Edition (64-bit) on Windows Server 2012 R2 Standard 6.3 <X64> (Build 9600: ) (Hypervisor)---------------------Apply 5014355 Security update for SQL Server 2016 SP3 GDR: June 14, 2022 to this SQL server instance.
Microsoft SQL Server 2016 (SP3-GDR) (KB5014355) - 13.0.6419.1 (X64) May 29 2022 21:05:29 Copyright (c) Microsoft Corporation Standard Edition (64-bit) on Windows Server 2016 Standard 10.0 <X64> (Build 14393: ) (Hypervisor) )------------------This the latest GDR for SQL server 2016 SP3.
Microsoft SQL Server 2019 (RTM-CU16-GDR) (KB5014353) - 15.0.4236.7 (X64) May 29 2022 15:55:47 Copyright (C) 2019 Microsoft Corporation Standard Edition (64-bit) on Windows Server 2019 Standard 10.0 <X64> (Build 17763: ) (Hypervisor)--------------This is the latest version for SQL server 2019.
If the answer is helpful, please click "Accept Answer" and kindly upvote it. If you have extra questions about this answer, please click "Comment".