I deployed (and re-deployed and redeployed) an AVD host pool. The tenant environment is hybrid, but the users that will be logging in aren't being synced with AD and only exist in the cloud. I had to add
enablecredsspsupport:i:0;authentication level:i:2;targetisaadjoined:i:1;
to the host pool RDP custom properties and then manually add the azure users with cmd to the remote desktop users group on the VM before it would even allow an AAD-only user to login.
Users added with net localgroup "remote desktop users" /add "AzureAD\******@domain.com"
I also tried adding them without the "AzureAD\" but got an error saying there is no such global user or group.
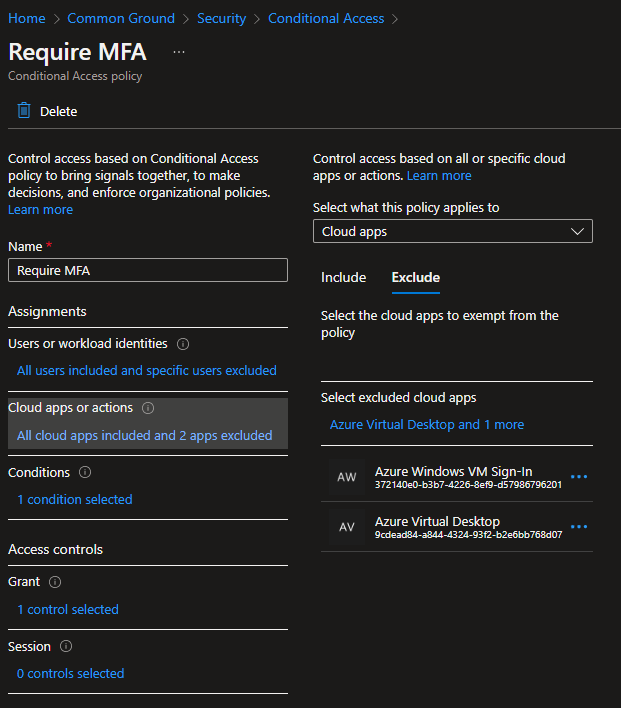
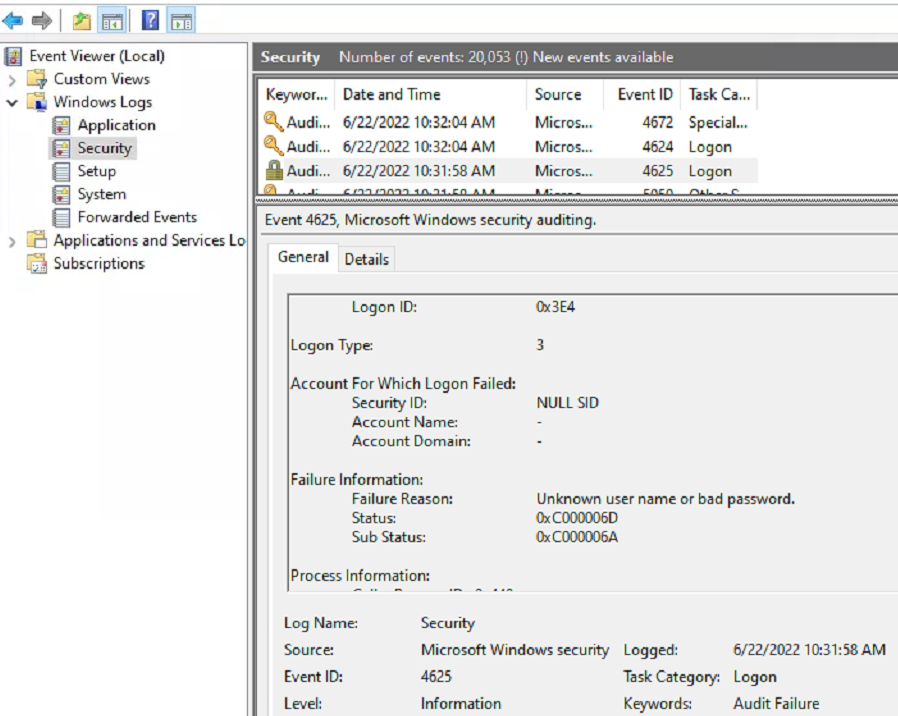
Users are able to log in via the web portal entering their username as "AzureAD\username@keyman .com". I've excluded the "Azure Windows VM Sign-in" and "Azure Virtual Desktop" from the CAP requiring MFA. My problem is that the users cannot login via the desktop client. These are remote users that will be using their own equipment and will require camera redirection (which isn't available in the web client). When signing in with the desktop client it allows signing into the app, but just spins when connecting to the session host displaying alternating "Initiating remote connection" and "Securing remote connection" messages. When refreshing the event log on the session host during the login attempt it's showing "Event 4625: Unkown user name or bad password". The other (but not as important) issue is that hybrid users that are synced with onsite-AD cannot log in via the web client or desktop client after being added in the same fashion. We don't need to be able to give them access at this point, but may be useful in the future.