Thank you my friend for advice. I find the reason:
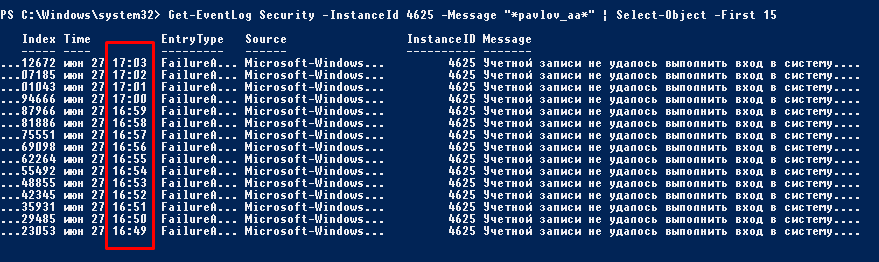
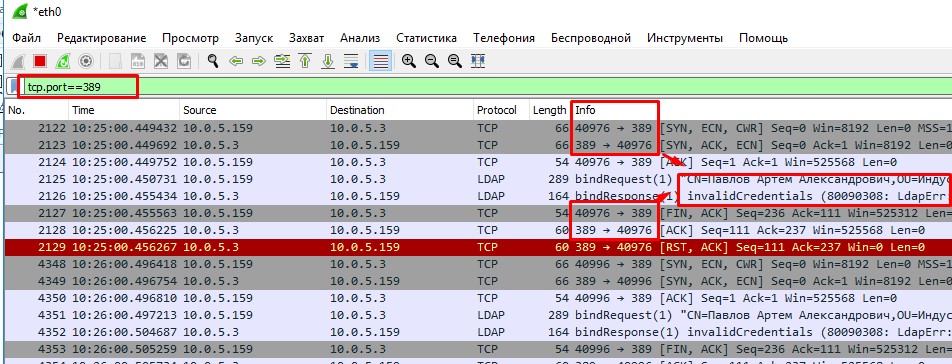
- I run on my server portable Wireshark with filter "tcp.port==389" - it's LDAP port on which a process send wrong creds. But to find this filter i start from "ip.dst==My_DC_IP" and find out that on my DC on 389 port arriving wrong creds.
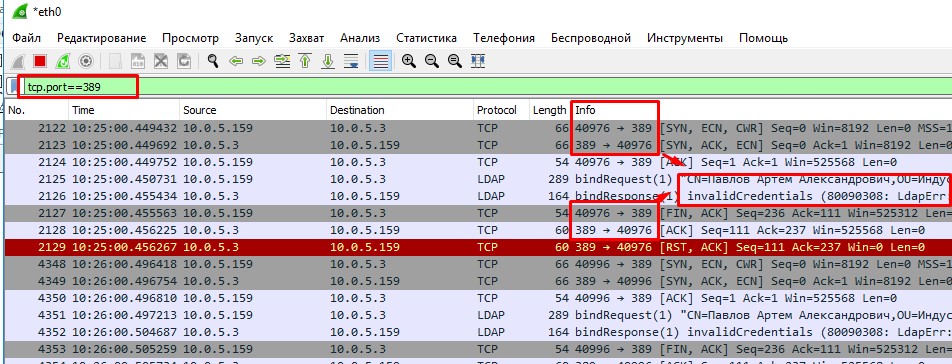
- I get range of ports from 418XX-419XX, ports changes every time, but i get a range. Also i have pretty cool timestamp - every 1 minute process try to send wrong creds on my DC.
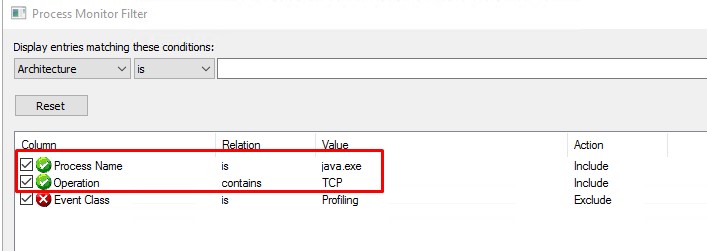
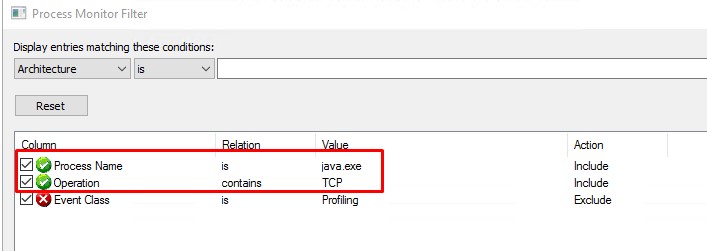
- I launch Procmon (with admin privs) from SysInternalSuite with filters for "java.exe" (i suspected it) adn what the most crucial "Operation contains TCP" to get rid off from non-network events
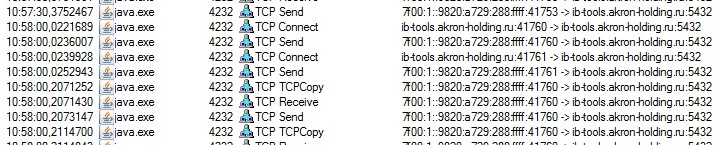
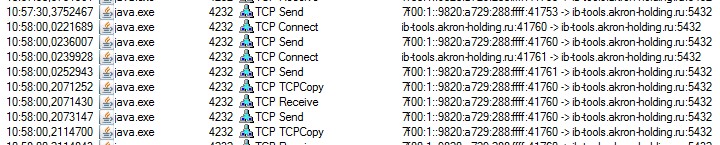
- I get a list network activity for Java and timestamps and ports range perfectly fit with what Wireshark showing me.
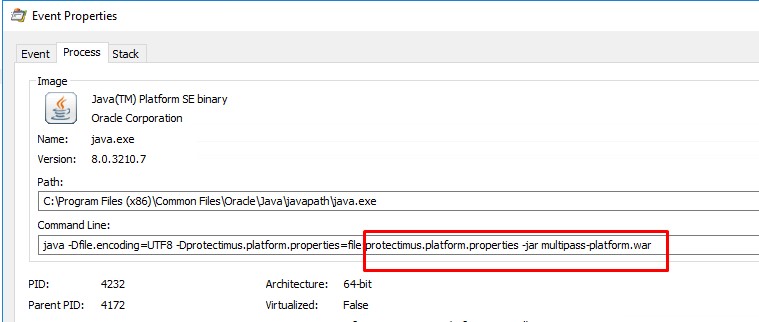
- I watch properties of Java process in Procmon and in commandline i see the culprit - Protectimus. Old, pilot project with trial licnese for 2FA. It was installed 1 year ago.
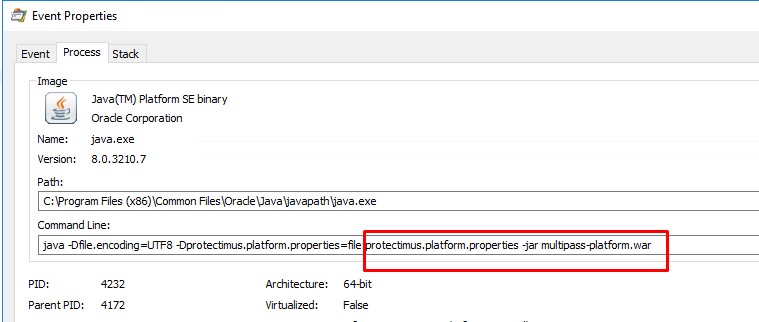
- I delete it and all problems are gone.
Old, abandoned programm with trial-license all the time try to establish connection with AD use wrong creds. 4625 Security event on my DC give me the ip-source of troublesome guy, but to find the process i need to start wireshark and procmon to find the reason.