Discrepency between AAD Single Log-Out docs/set-up page fields & real life.

I have been using the documentation located at: https://learn.microsoft.com/en-us/azure/active-directory/develop/single-sign-out-saml-protocol to enable the SAML Single Sign-Out profile.
I have created an Enterprise Application (EA) on the AAD portal.
My application's SAML metadata is:
<m:EntityDescriptor entityID="max-test" ID="_0b4fa43e-1e1c-4fa9-a4d6-adcf246b53bc" xmlns:m="urn:oasis:names:tc:SAML:2.0:metadata">
<m:SPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol" WantAssertionsSigned="true">
<m:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://localhost:5001/saml/slo/logout" ResponseLocation="https://localhost:5001/saml/slo/response" />
<m:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://localhost:5001/saml/consumer" index="0" isDefault="true" />
<m:AttributeConsumingService index="0" isDefault="true">
<m:ServiceName xml:lang="en">BlaBla</m:ServiceName>
<m:RequestedAttribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic" isRequired="true" />
<m:RequestedAttribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic" isRequired="true" />
<m:RequestedAttribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic" isRequired="true" />
</m:AttributeConsumingService>
</m:SPSSODescriptor>
</m:EntityDescriptor>
I have selected "SAML" as the "Single Sign-On mode" on the EA. I then uploaded my application's metadata file. This is where the first problem began:
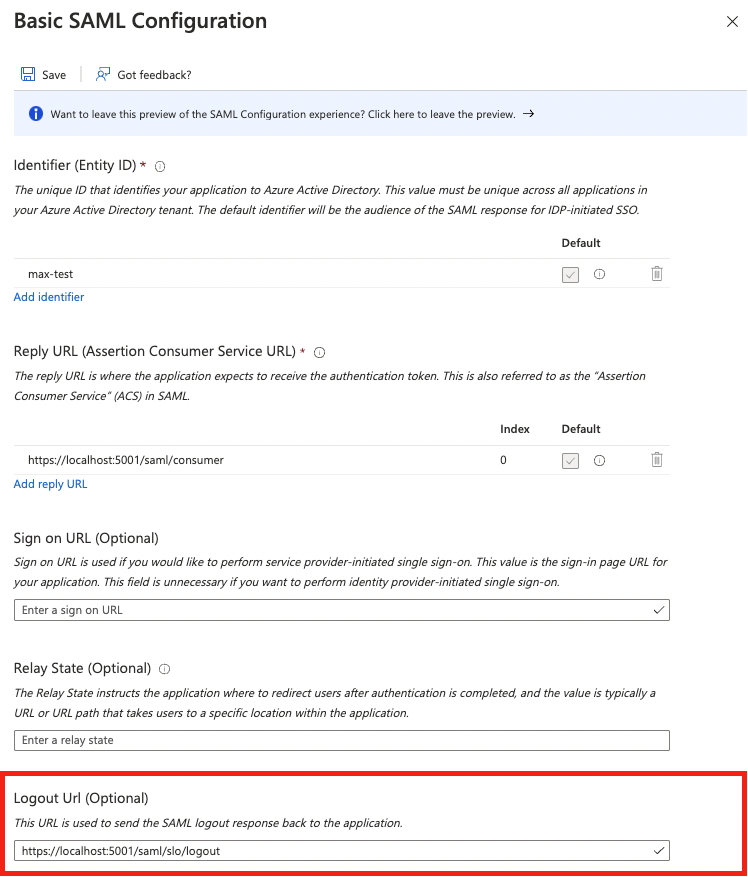
According to the description of the Logout Url right there in the screenshot as well as in the docs linked at the top, the Logout Url "is used to send the SAML logout response back to the application" i.e. "Azure AD sends a LogoutResponse to the applications LogoutURL". As per my metadata that URL should be https://localhost:5001/saml/slo/response.
It looks like it instead picked the SP's Single Logout Service URL, which expects to receive LogoutRequests for example when user has signed out from another application but this application was in the same session. (This will turn up to be true, as shown in a second). It also baffled me that this SP Single Logout Service URL that receives LogoutRequests from the IdP was not configured anywhere else.
Anyway, I hit save. I was then able to log in via SSO fine. All looks good. I then tried to log out.
My application generated the following LogoutRequest & sends it to AAD's SingleLogoutService as defined in the IdP's metadata:
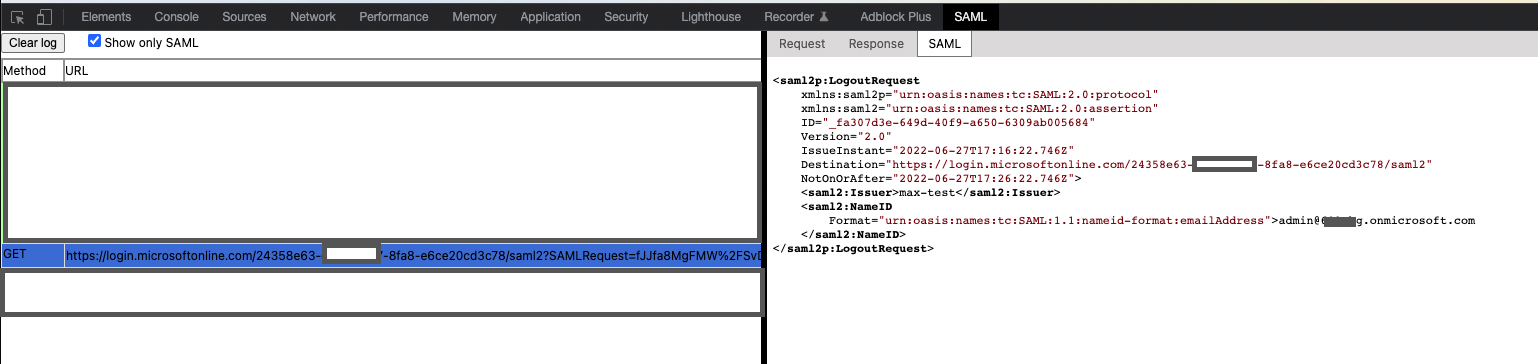
And here is the second problem. According to the documentation, I should now receive back a LogoutResponse to my app.
Further, the doc specifies that "If one of the other participants sends a LogoutRequest to Microsoft identity platform (the session authority), then Microsoft identity platform will send a LogoutRequest back to all the session participants except the participant which sent the initial LogoutRequest."
Unfortunately both these statements are false. AAD never responds back to my request with a response. It instead sends it's own LogoutRequest back to my application at the Logout Url we saw earlier:
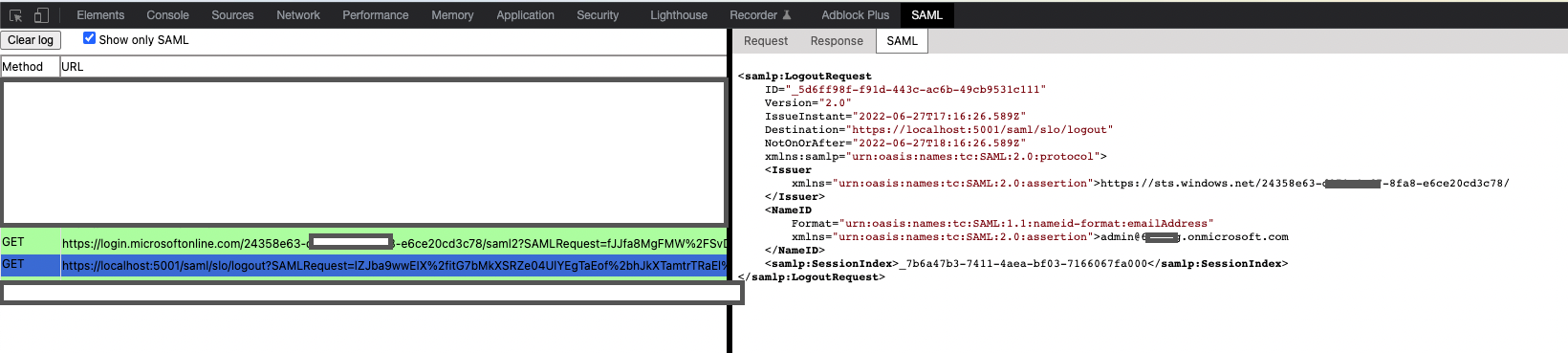
To which my app responds with a LogoutResponse as per spec:
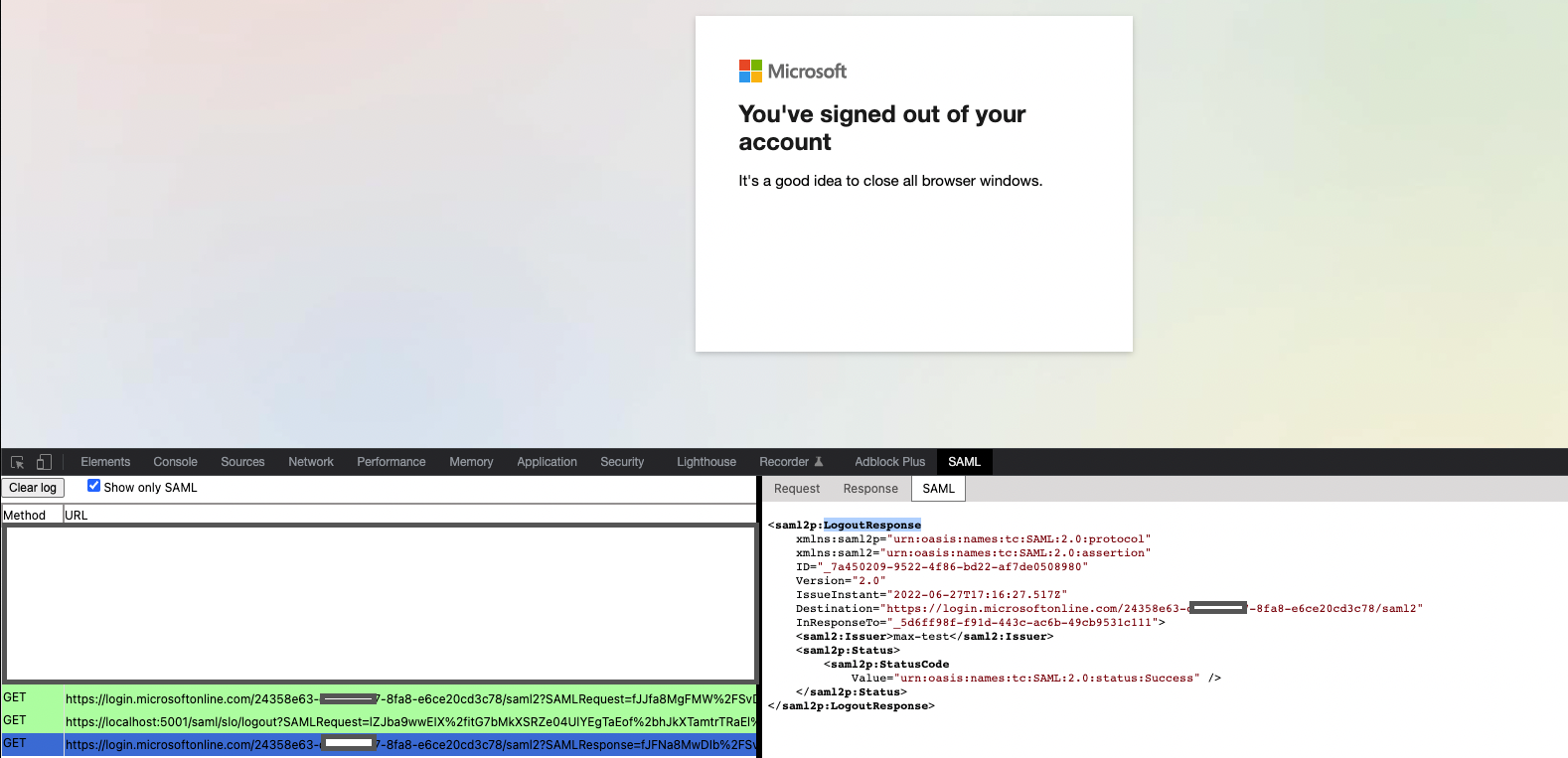
I have also carried out a test where I sign out of the entire SSO session directly via the IdP - in this case, AAD correctly sends a LogoutRequest to the /saml/slo/logout endpoint to log out the current user.
To summarise:
- The
Logout Urlis populated from the wrong metadata field. - The
Logout Urlis used as if it were theSingle Logout Url- the URL to which sendLogoutRequests. The configuration of this URL should be a new field. The docs should be updated to explain the 2 fields better. - During Single Sign-Out, AAD incorrectly sends a
LogoutRequestto the application which initiated the Sign-Out process. - AAD never replies back to the initial
LogoutRequestwith aLogoutResponse
I am fairly new to SAML & especially to AAD, so if i am mistaken somewhere, please point it out.
If I am correct, can we fix/update the functionality of AAD SSO & update the documentation.
Thank you :)
