Hello @Anoop Mohanan-FT ,
I understand that you would like help in creating a WAF exclusion rule in AFD for the below scenario:
ruleName_s : DefaultRuleSet-1.0-RFI-931130
Action: Block
Matched Data: https://domainname found within QueryParamValue:redirect_uri: https://domainname/signin-oidc
details_matches_s:
[
{
"matchVariableName": "QueryParamValue:redirect_uri",
"matchVariableValue": "https://domainname/signin-oidc"
}
]
Per design, the values of the fields you use aren't evaluated against WAF rules, but their names are evaluated.
So, if a header value, cookie value, post argument value, or query argument value produces false positives for some rules, you can exclude that part of the request from consideration by the rule as below:
If WAF logs shows - QueryParamValue:SOME_NAME, then the WAF exclusion should be - Query string args name Equals SOME_NAME
Refer : https://learn.microsoft.com/en-us/azure/web-application-firewall/afds/waf-front-door-exclusion#define-exclusion-based-on-web-application-firewall-logs
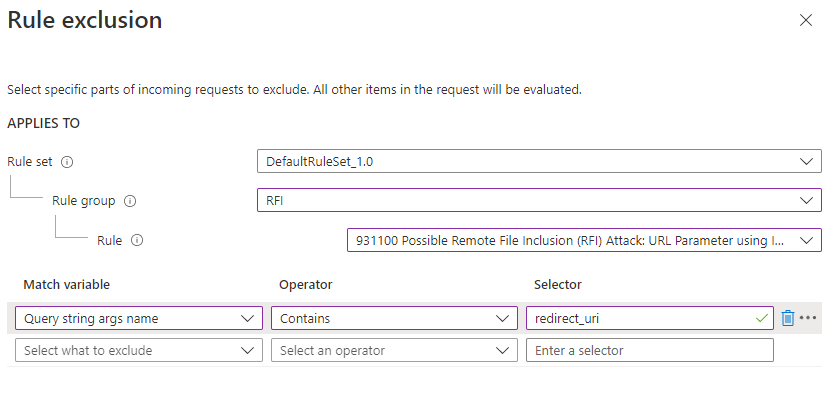
In your case, it is QueryParamValue:redirect_uri, so the WAF exclusion rule should be Query string args name Equals redirect_uri.
You can apply exclusion lists to all rules within the managed rule set, to rules for a specific rule group, or to a single rule.
Since, the block is triggering for DefaultRuleSet-1.0-RFI-931130, we need to select that particular RFI rule in the WAF exclusion config as below:
Kindly let us know if the above helps or you need further assistance on this issue.
----------------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.