The third-party provider does not send mails, these are sent by M365. The problem affects incoming mail traffic.
The mail flow is like this at the customer SNSF:
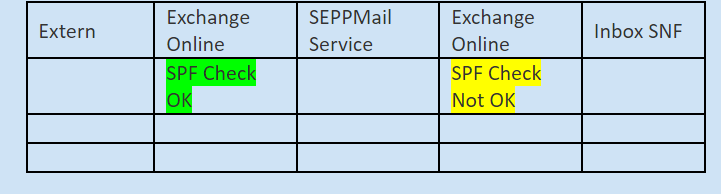
The SEPPMail service is an email encryption and signature gateway.
Because the mails are sent to this service via Transport Rules, the SPF Check fails when they arrive back at Exchange Online, as this service is logically not considered a valid sender system for the external domain.
Question:
Can I exclude mails that come from the SEPPMail service (specific Inbound Connetor) from this SPF check, or generally from the anti-spam check, because this was already carried out before, when the message arrived for the first time.
Or can I e.g. set a header that causes an antispam bypass when the message comes back to avoid a double scan?
