Let me break this down a bit:
You have the AWD data connector enabled. That connector creates three tables including AWSVPCFlow. This table provides a source and destination IP address.
You are seeing IPs in this table that appear to be malicious. Yes? Which threat intelligence provider are you using to reach the verdict? Do you have these same IPs listed as indicators in the Sentinel Threat Intelligence section?
Sentinel has two primary TI mapping options. The first is a Microsoft Threat Intelligence rule comparing Security Graph IOCs to a limited set of tables. The second is a bring-your-own-TI solution. You add indicators manually or automatically using TAXII or an API-based connector. The Threat Intelligence section in the portal. These indicators are mapped to various entities by "TI Map" rules available in the analytic rule templates.
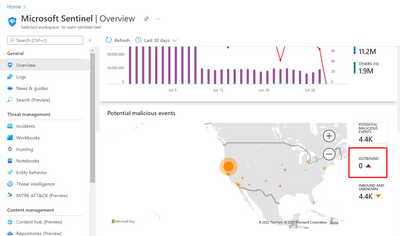
You may be referring to the malicious IP mapping seen in the overview page. Thie is a non-alerting enrichment that happens on the backend for a limited set of tables. No options are provided to customize this view. Nice to look at but largely pointless due to the limited scope and lack of alerts. You won't see AWSVPCFlow here any time soon.
There is a "TI map IP entity to AWSCloudTrail rule template. This checks the AWSCloudTrail table for IP indicators that have been collected in the Threat Intelligence section. You need to set up a TI feed for this to be effective. The rule does not look at the AWSVPCFlow table. You could use this rule as an example and create a custom rule for AWSVPCFlow if these IPs are not part of the AWSCloudTrail table.
So currently, no TI mapping on AWSVPCFlow but it would not be too difficult to configure.