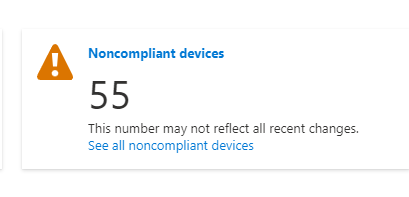
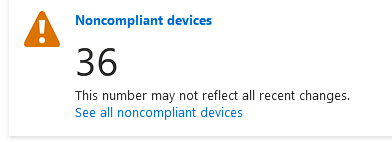
I am experiencing a similar issue. The devices are showing as non compliant. However, there are no policies that reflect this finding. Can anyone shed some insight into this issue?
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
I have a number of devices that are showing up as Not Compliant in our Azure AD devices view, they are all Azure AD Registered and none of them are managed by InTune, so I am trying to determine: Why are they marked as Non-Compliant and how can I fix this?
I am experiencing a similar issue. The devices are showing as non compliant. However, there are no policies that reflect this finding. Can anyone shed some insight into this issue?



Just for interest, in case it affects anyone else, we also recently found hybrid Azure devices (domain-joined Win 10 machines) in a non-MDM/Intune environment that were showing as non-compliant. All joined since the 30th of November. Previously-joined devices were showing as N/A as expected.
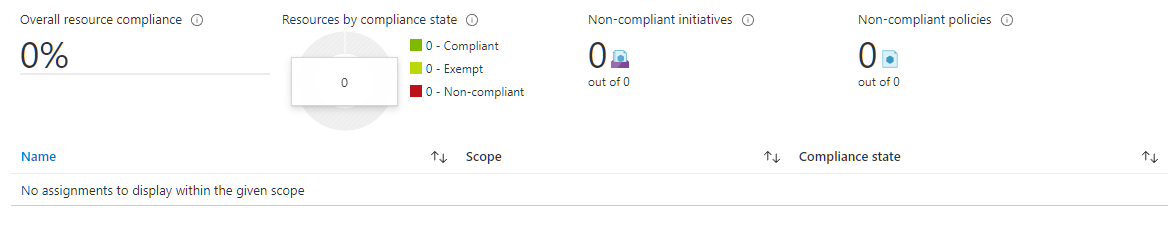
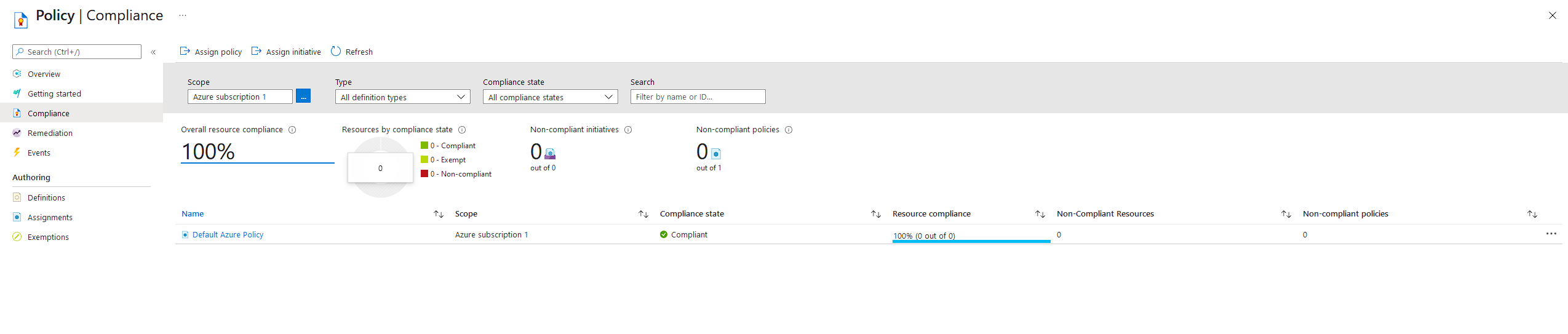
After locating the never-used Policy page in Azure Portal (https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/), I found the ASC Default policy (part of Defender for Cloud) has somehow become enabled on our main subscription. It seems that some Defender for Cloud trial licenses got assigned and resources in the subscription came into scope.
What exactly happened with this feature and policy being enabled is still unclear, but for us, it is this ASC Default policy applied in the subscription that is causing the most recently-joined machines to be marked as "non-compliant".
Nothing can possibly be compliant with this policy in our environment, since it hasn't been designed for it - we don't use Defender for Cloud.
I note that last month "Governance Rules at Scale" was released into Preview for Defender for Cloud, where bulk rules can be configured at subscription, connectors or various scopes. I wonder if these changes may have suddenly "activated" this policy, at least for us.

Hi @BK , the best place to start for this is here. Please look through this and it should help with finding the cause. And then fixing it should come easily. If you're still having issues please let me know and I can help you further!
If this answer helped you please mark it as "Verified" so other users can reference it.
Thank you,
James
@James Hamil We have no Azure Policy set up.
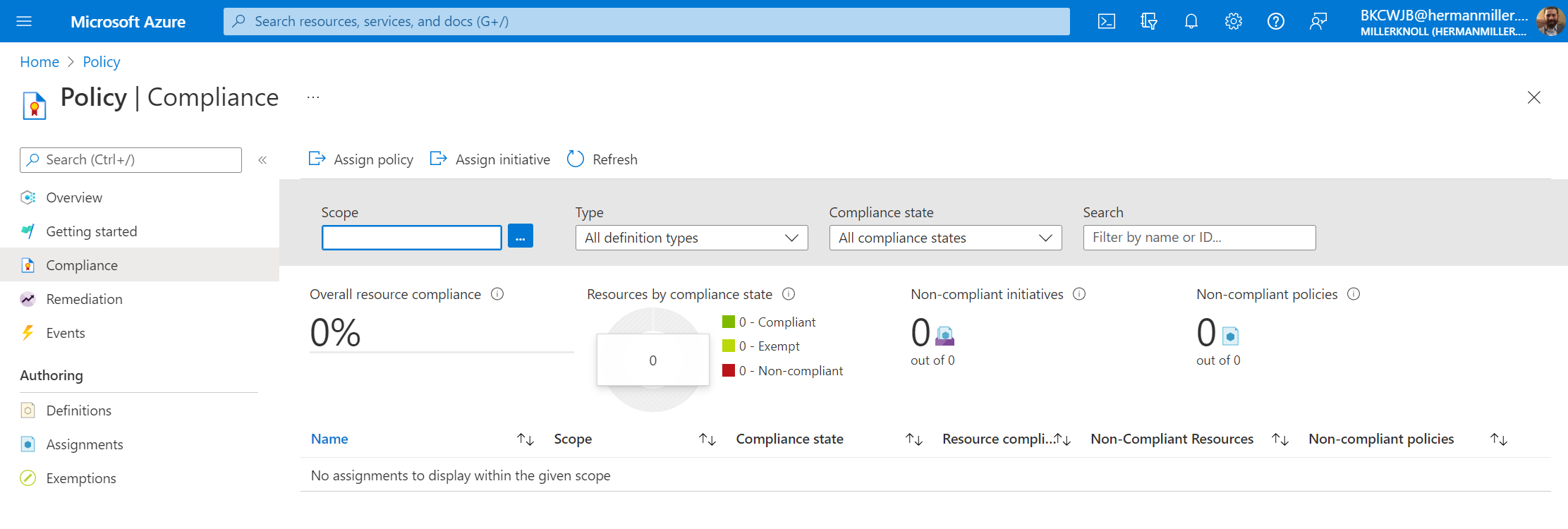
Any other thoughts? Also, our Non-Compliant devices has increased in number to 224 from the original post.
We have a similar issue.