Hello BmoreOS
Considering the source of the infection, it may be not possible to retrieve the root cause of the infection of vector, instead just that the code added to the system in some way, most times even unadverted to the user.
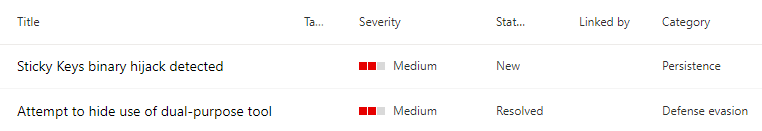
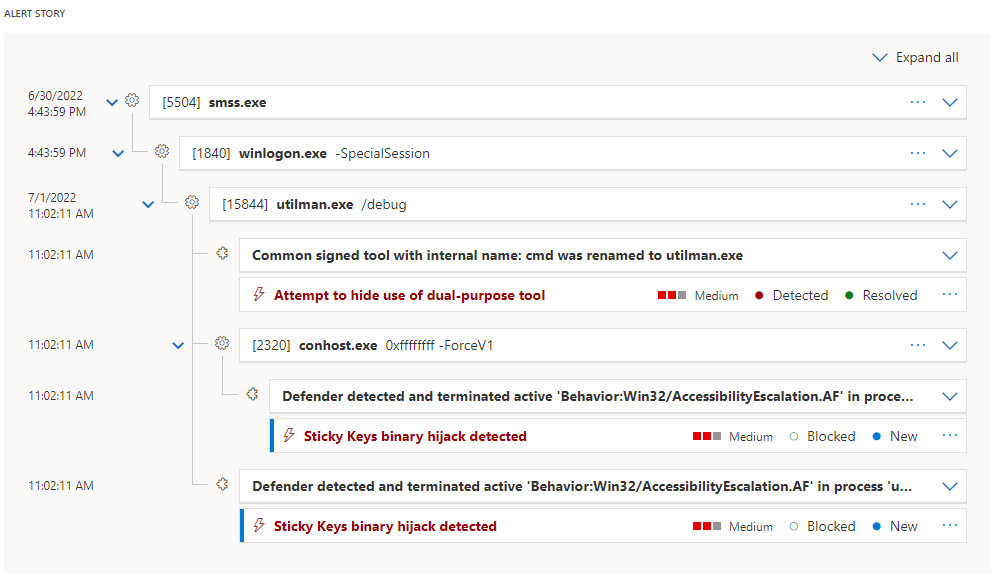
In the case that you suspect system manipulation from the user, you can verify if the file SETHC.EXE if it matches the size of the CMD.EXE (mechanism of the exploit) and retrieve data such as time of the file modification and in some cases will appear the user. However, this should not set enough proof to blame the user, as some infections may act in the same environment session of the user.
In case you want to fully proctect the systems, you can use the registry editor and change the Permissions for that registry chain only to the Administrator. The path and key for disabling Sticky Keys is:
HKEY_CURRENT_USER\Control Panel\Accessibility\StickyKeys\Flags=”506″ (by default the value is 510)
----------------------------------------------------------------------------------------------------------------------------------------
--If the reply is helpful, please Upvote and Accept as answer--