Hello @aheilmaier ,
I understand that you would like to know how you can propagate more specific routes via Azure VPN gateway to your onprem/local gateway.
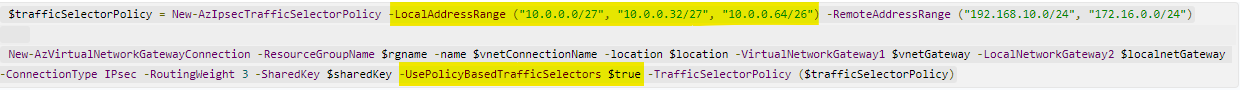
I believe you are referring to the "Traffic from Azure to on-premises networks" section of the below doc:
https://learn.microsoft.com/en-us/azure/vpn-gateway/site-to-site-vpn-private-peering#traffic-from-azure-to-on-premises-networks
That section talks about how you can influence the routing of traffic from Azure to on-prem networks but the changes or requirements mentioned in it are not done on Azure side. They are done on your on-prem side.
It says "to ensure that the IPSec path is preferred over ExpressRoute, you should advertise more specific network prefixes on the VPN BGP session", which means - you need to advertise more specific prefixes from your on-prem VPN device over the VPN session and advertise less specific prefixes over ExpressRoute BGP session. So, that Azure will receive both these routes via BGP but will select the specific prefix and take the VPN/IPSec path because Azure always selects a route using LPM (Longest Prefix Match) algorithm.
Refer : https://learn.microsoft.com/en-us/azure/virtual-network/virtual-networks-udr-overview#how-azure-selects-a-route
By design, the Azure VPN gateways advertise the following routes to your on-premises devices and you cannot exclude these:
- Your virtual network address prefixes.
- Address prefixes for each local network gateway connected to the Azure VPN gateway.
- Routes learned from other BGP peering sessions connected to the Azure VPN gateway, except for the default route or routes that overlap with any virtual network prefix.
Kindly let us know if the above helps or you need further assistance on this issue.
----------------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.