Hello,
Thank you so much for posting here.
Whatever hash algorithm you choose under the Select the hash algorithm for signing certificates issued by this CA determines how the root CA's own CA certificate is signed and how it will, by default, sign other certificates and CRLs it issues.
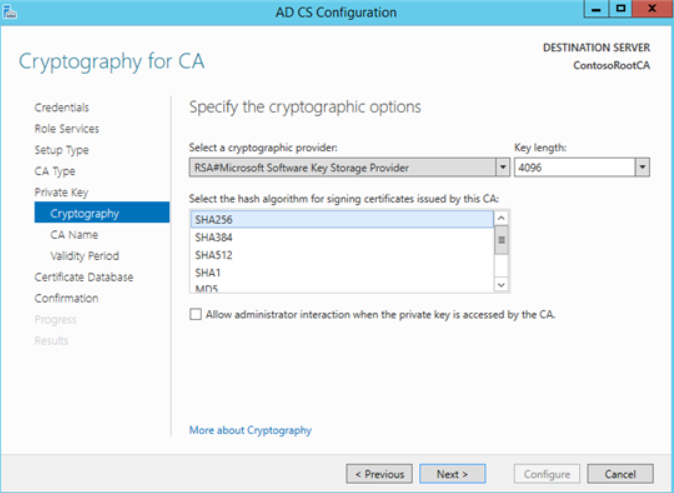
Some applications supporting SHA-2 have problems with the larger SHA-2 key sizes, such as SHA-512. For example, TLS 1.2 supports SHA-256 and SHA-384, but not SHA-512.
Here are some relevant links:
https://social.technet.microsoft.com/Forums/en-US/b6ffa278-4a04-4609-ac35-8390f5ba9cb6/ldap-over-ssl-on-windows-2012r2-server-dcs-tls-12-not-working?forum=winserversecurity
https://ucken.blogspot.com/2013/12/schannel-errors-on-lync-server.html
https://learn.microsoft.com/en-us/archive/blogs/silvana/schannel-errors-on-scom-agent
For more information, we could refer to:
Implementing SHA-2 in Active Directory Certificate Services
https://social.technet.microsoft.com/wiki/contents/articles/31296.implementing-sha-2-in-active-directory-certificate-services.aspx
We could kindly have a check of the provided information to evaluate the limitation of SHA 512.
Please note: Information posted in the given link is hosted by a third party. Microsoft does not guarantee the accuracy and effectiveness of information.
Best regards,
Hannah Xiong
============================================
If the Answer is helpful, please click "Accept Answer" and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.