
Could any issues arise from denying "Full Control" or "Read" permissions to the majority of users (No built-in & no admins) on the domain root ACL (mic.com) tree from ADUC? if yes, what are the issues?
Maybe, if you are assigning the permissions to a group, then you have the ability to remove\change permissions if any issues are found, just make sure that you don't add any of your admins or service account to the group. By using Deny Full Control, rather than blocking specific attributes, you are preventing a user from reading the attributes on their own user object, which could cause problems. As to what the issues will be it's difficult to tell, as it will depend on what applications and services you are running in your environment and what access they require to the AD. As always you will need to test if these changes cause any issues.
Why Microsoft default permissions are enabling AD objects enumeration?
One of the original intents for AD was to provide an open directory service which could be used to store and share information within organizations, unfortunately 20+ years later this openness can be used by bad actors to compromise the environment. The other possible reason, by providing a more open permission set, it simplified the adoption of Active Directory, back in the day when NetWare was king but more complicated to implement.
Is there another best practice to prevent user enumeration in AD environment?
I don't believe Microsoft have published anything specifically, their security models are based around delegation and tiering of roles, rather than preventing users from reading objects or attributes.
One thing to bear in mind with this approach, it may not work as you expects, as the deny permissions set at the root of the domain, maybe not be enforced lower down the OU structure. As an explicit allow will take precedence over an inherited deny permission. The default permissions for an OU has authenticated user List and Read.
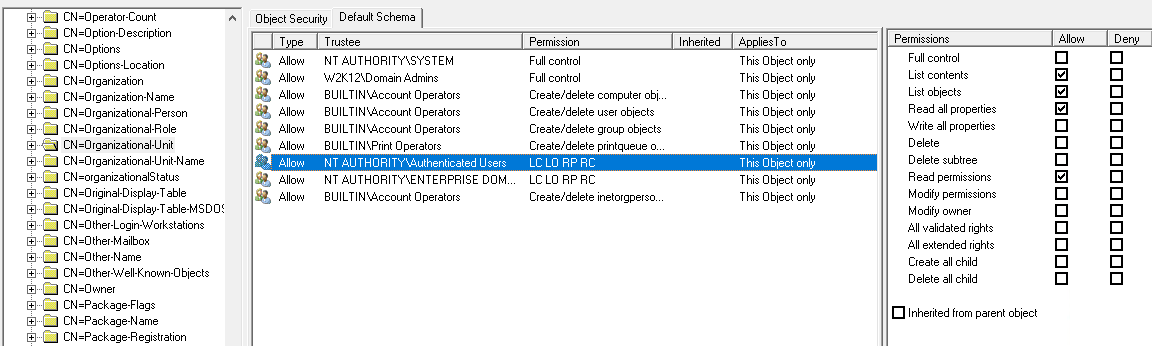
Also with groups and users protected by the SDProp process, permissions set on root will not be applied to these objects, you will need to set these permissions on the AdminSDHolder, but update these permissions with caution, as there is potential to lock yourself out of the AD.
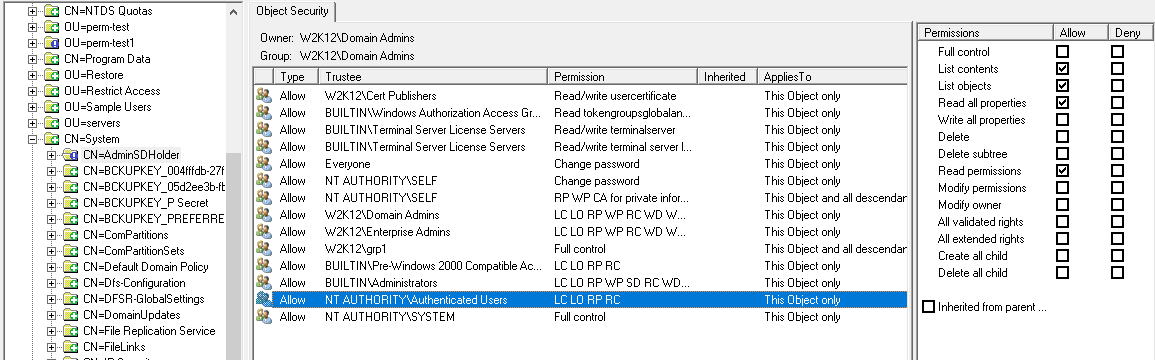
With AD you have the ability to change the permissions to whatever your want and define your own access model, however, MS will only test new features and updates based on the default permissions. As with any changes, document the changes, so the next person to manage the environment know what has been changed.
Gary.

