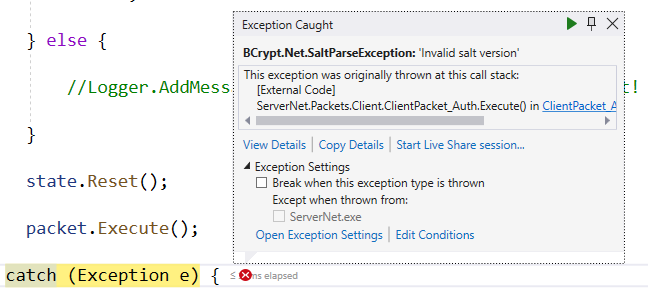
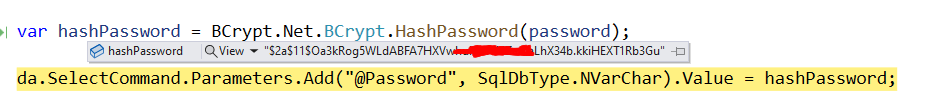
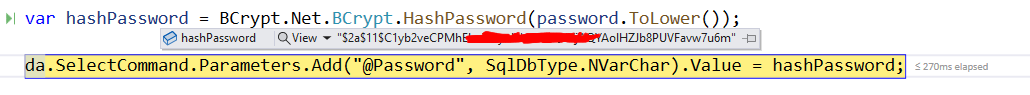
According to the documentation, the salt is part of the results from HashPassword(). If you did not create a salt then you are using the default salt created by HashPassword(). I have no idea as I cannot see your code.
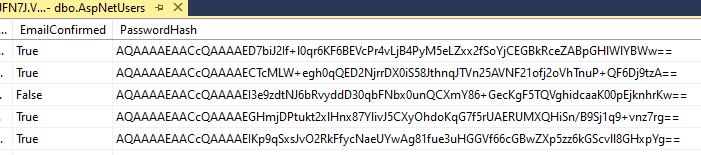
The steps should be very simple. Get the hash and store the hash in the database along with the username so you can fetch the hash later.
string passwordHash = BCrypt.Net.BCrypt.HashPassword("Pa$$w0rd");
To validate the login, fetch the hash from the database using the username then validate the hash.
bool verified = BCrypt.Net.BCrypt.Verify("Pa$$w0rd", passwordHashFromTheDatabase);
The salt is stored in the front of the hash string. If you look at my example I removed the first character in the string which caused the salt error.
bool verified = BCrypt.Net.BCrypt.Verify("Pa$$w0rd", passwordHash1.Substring(1, passwordHash1.Length-1));
Anyway, if you followed the simple steps above and still get a salt error then I assume there is something else wrong with your code. It could be how the hash is passed, saved, or fetched. You also mentioned a proxy but have not explained how the proxy handles the hash.
You'll need to troubleshoot your code now that you have a better understanding of how BCrypt works.