Basically, sign-in logs are generated in Operating System level, it means you have to collect the events somehow somewhere. Azure Monitor and its Azure Monitoring Agent provide the capability to collect security logs without Microsoft Defender for Cloud enabling. But it's required to install the agent and configure Log Analytics workspace to collect the event logs. After completing the task, you will be able to create alerts based on your query.
Monitor security events in Azure Virtual Machine
Hello Team,
I'm looking way to Monitor Azure VM Sign-in logs. I need to set an alert if any user try to RDP into Azure VM it should get fired with his name with Computer name,Date and Time.
The SecurityEvent command is not working in Azure Monitor Log analytics Workspace. Also, I found Azure Monitor is not integrated with security Events.
Anyone knows other way to get alert if RDP users Successful sign-in. The below is predefined Query in Log Analytics workspace but it wont work on Azure VM.
SecurityEvent
| where EventID == 4624
| summarize arg_max(TimeGenerated) by Computer
Azure Monitor
Azure Virtual Machines
-
 Maxim Sergeev 6,586 Reputation points Microsoft Employee
Maxim Sergeev 6,586 Reputation points Microsoft Employee2022-08-03T17:01:22.263+00:00
1 additional answer
Sort by: Most helpful
-
George Moise 2,361 Reputation points Microsoft Employee
2022-08-09T11:42:36.577+00:00 Hello,
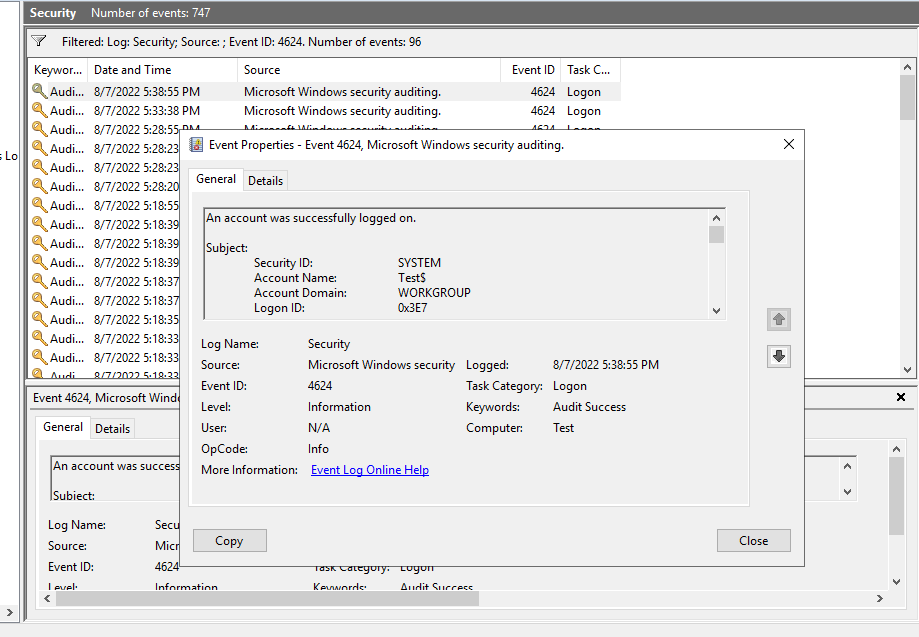
When a user is successfully connecting remotely (RDP - TCP 3389) to a Windows Operating System, an event with EventID 4624 will be generated in that Operating System - Security Event Log.
In that Event, the LogonType will be 10 (RemoteInteractive).Now, if you want to collect those events in the SecurityEvent table of a Log Analytics Workspace, you will need to follow the bellow note from this article :
"You can't configure collection of security events from the workspace using Log Analytics agent. You must use Microsoft Defender for Cloud or Microsoft Sentinel to collect security events. Azure Monitor agent can also be used to collect security events."
- If you are using Microsoft Sentinel, then you can enable the Security Event data Connectors (either the "old" one via Log Analytics Agent or the new one via the Azure Monitor Agent) and once the events are collected, you can create there an Analytic (detection) Rule.
- If you are using Defender for Cloud, then you can configure from there that your agents will push events from the Security Event Logs, and then you can simply create an Azure Monitor Alert Rule.
Without Sentinel or Defender for Cloud, from a simple Log Analytics Workspace, you cannot collect the Security Events.
I hope it helped.
Let me know if more info is required.BR,
George