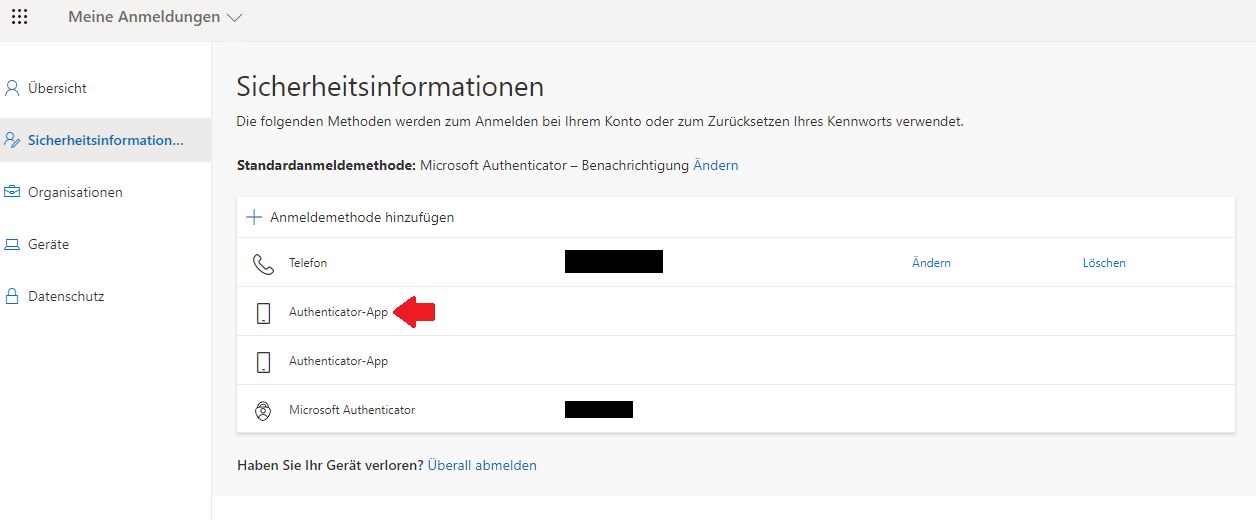
As per your work around another global admin can delete the MFA methods from within the Azure AD. Go to the User > Authentication Methods > Change to Preview Mode if in Legacy View, then you see a list of the user's MFAs. You can then delete the method in question.
You had to create a temporary global admin user since my tenant had only one regular global admin aside from the emergency admin account (whose login details are in a bank vault).
Also, now you are able to login to https://mysignins.microsoft.com/ without 2FA, and as soon as I access https://mysignins.microsoft.com/security-info I get prompted for 2FA, and the delete buttons are present.
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.